(RM Jr of worm fame was just a kid then.)
AFAIK the only group to discover Ken’s hack was us in PWB/UNIX. One of the other guys noticed C prepreprocessor had gotten bigger, looked at binary namelist, found symbol not in source code. I got onto Ken’s system, found the code, very clever.
(RM Jr of worm fame was just a kid then.)
More chortling, then (must have been Bob): uhh, NSA really doesn’t have sense of humor.
We did audit, agreed with that, BUT:
1) Many terminals had yellow stickies with root password.
2) They’d reused unused lab space w/o adequate HVAC, room got hot, so they often left door open.
As usual, good tech helps, but human error/laziness must always be guarded against.
Same thing happened later with workstations & then PCs: user depts got impatient with central IT.
Just as happened later with workstations/PCs, BTL Directors found that running own computer center well was a pain. The main computer centers then offered to do facilities management, with good HVAC,
I recall centralized mainframe service bureaus of 1960s,reborrn as cloud🙂
More from Software
@JuliaLMarcus @Iplaywithgerms This paper gives documentation on software (with causal reasoning, assumptions reviewed in appendix) for a parametric approach to estimating either "total effects" or "controlled direct effects" with competing events and time-varying
@Iplaywithgerms Total effects capture paths by which treatment affects competing event (e.g. protective total effect of lifesaving treatment on dementia may be wholly/partially due to effect on survival). Controlled direct effects do not capture these paths
@Iplaywithgerms More detailed reasoning on the difference and tradeoffs between total and controlled direct effects and causal reasoning in the point treatment context provided here along with description of some estimators and
@Iplaywithgerms If you are familiar with more robust approaches like IPW or even better TMLE for time-varying treatment, these are trivially adapted to go after the controlled direct effect by simply treating competing events like loss to follow-up (censoring). e.g.
@Iplaywithgerms Examples of IPW estimation of the total effect of a time-varying treatment described in Appendix D of this paper:
https://t.co/RNhcgTBMkb
And here
https://t.co/rMWmwFBWwV
Others in reference lists of above papers.
@Iplaywithgerms Total effects capture paths by which treatment affects competing event (e.g. protective total effect of lifesaving treatment on dementia may be wholly/partially due to effect on survival). Controlled direct effects do not capture these paths
@Iplaywithgerms More detailed reasoning on the difference and tradeoffs between total and controlled direct effects and causal reasoning in the point treatment context provided here along with description of some estimators and
@Iplaywithgerms If you are familiar with more robust approaches like IPW or even better TMLE for time-varying treatment, these are trivially adapted to go after the controlled direct effect by simply treating competing events like loss to follow-up (censoring). e.g.
@Iplaywithgerms Examples of IPW estimation of the total effect of a time-varying treatment described in Appendix D of this paper:
https://t.co/RNhcgTBMkb
And here
https://t.co/rMWmwFBWwV
Others in reference lists of above papers.
forgive my indulgence but 2020's been a big year for @shmuplations, so here's a look back at everything that went up over the last twelve months—there's a lot of stuff I'm sure you all read & other things you'd be forgiven for missing, so let's recap (thread)
the year kicked off with shmuplations' first big video project: a subtitled translation of a 2016 NHK documentary on the 30th anniversary of Dragon Quest which features interviews with Yuji Horii, Koichi Nakamura, Akira Toriyama, and Koichi Sugiyama https://t.co/JCWA15RTlx

following DQ30 was one of the most popular articles of the year: an assortment of interviews with composers Yuzo Koshiro and Motohiro Kawashima concerning the music of Streets of Rage 1, 2 & 3 https://t.co/QUtyC9W12Z their comments on SoR3 in particular were full of gems

Game Designers: The Next Generation profiled six potential successors to the likes of Shigeru Miyamoto & Hironobu Sakaguchi, some of who you may recognise: Kazuma Kaneko, Takeshi Miyaji (1966-2011), Noboru Harada, Kan Naitou, Takashi Tokita & Ryoji Amano https://t.co/lWZU3PLvwX

from the 2010 Akumajou Dracula Best Music Collections Box, a subbed video feature on long-time Castlevania composer Michiru Yamane https://t.co/NMJe4ROozR sadly, Chiruru has since passed; Yamane wrote these albums in his honor
https://t.co/orlgPTDsKK
https://t.co/QnQl8KI9IX

the year kicked off with shmuplations' first big video project: a subtitled translation of a 2016 NHK documentary on the 30th anniversary of Dragon Quest which features interviews with Yuji Horii, Koichi Nakamura, Akira Toriyama, and Koichi Sugiyama https://t.co/JCWA15RTlx

following DQ30 was one of the most popular articles of the year: an assortment of interviews with composers Yuzo Koshiro and Motohiro Kawashima concerning the music of Streets of Rage 1, 2 & 3 https://t.co/QUtyC9W12Z their comments on SoR3 in particular were full of gems

Game Designers: The Next Generation profiled six potential successors to the likes of Shigeru Miyamoto & Hironobu Sakaguchi, some of who you may recognise: Kazuma Kaneko, Takeshi Miyaji (1966-2011), Noboru Harada, Kan Naitou, Takashi Tokita & Ryoji Amano https://t.co/lWZU3PLvwX

from the 2010 Akumajou Dracula Best Music Collections Box, a subbed video feature on long-time Castlevania composer Michiru Yamane https://t.co/NMJe4ROozR sadly, Chiruru has since passed; Yamane wrote these albums in his honor
https://t.co/orlgPTDsKK
https://t.co/QnQl8KI9IX

You May Also Like
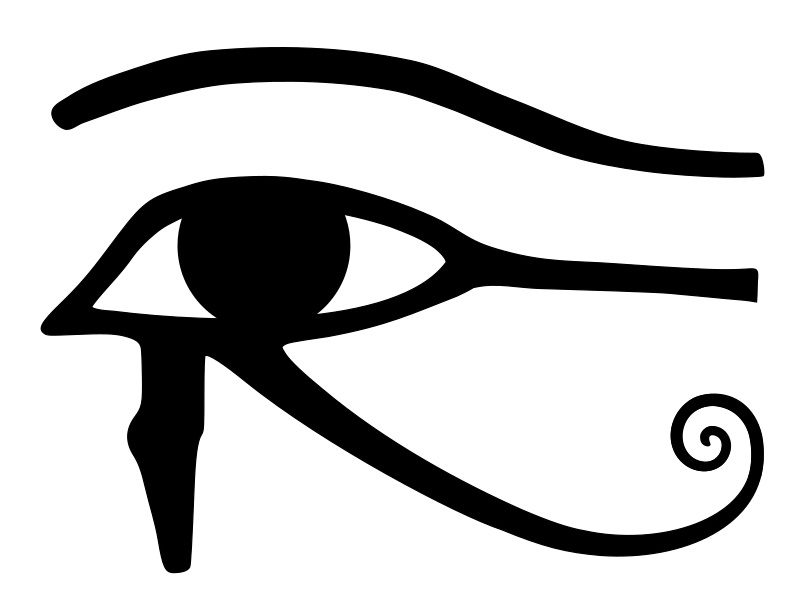
The Eye of Horus. 1/*
I believe that @ripple_crippler and @looP_rM311_7211 are the same person. I know, nobody believes that. 2/*
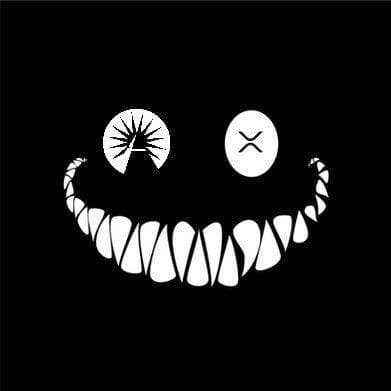
Today I want to prove that Mr Pool smile faces mean XRP and price increase. In Ripple_Crippler, previous to Mr Pool existence, smile faces were frequent. They were very similar to the ones Mr Pool posts. The eyes also were usually a couple of "x", in fact, XRP logo. 3/*
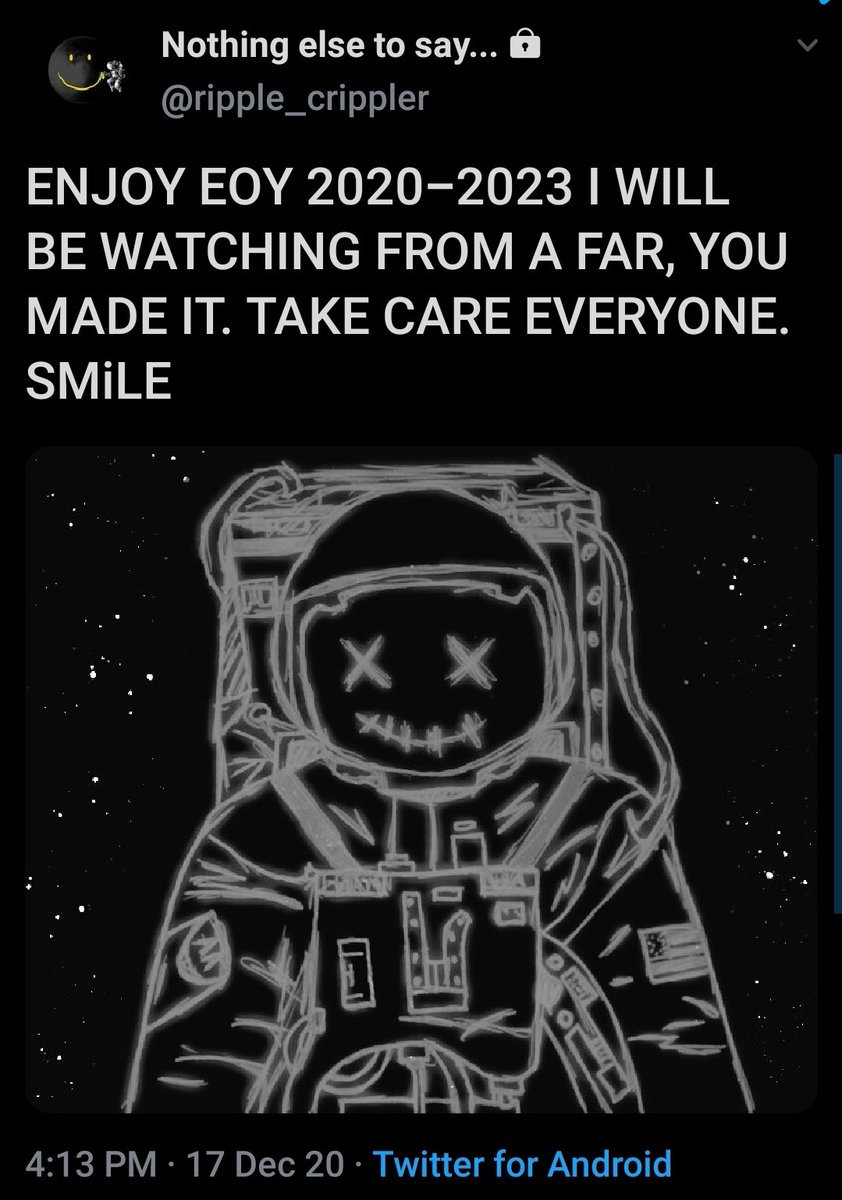
The smile XRP-eyed face also appears related to the Moon. XRP going to the Moon. 4/*
And smile XRP-eyed faces also appear related to Egypt. In particular, to the Eye of Horus. https://t.co/i4rRzuQ0gZ 5/*

I believe that @ripple_crippler and @looP_rM311_7211 are the same person. I know, nobody believes that. 2/*
Today I want to prove that Mr Pool smile faces mean XRP and price increase. In Ripple_Crippler, previous to Mr Pool existence, smile faces were frequent. They were very similar to the ones Mr Pool posts. The eyes also were usually a couple of "x", in fact, XRP logo. 3/*

The smile XRP-eyed face also appears related to the Moon. XRP going to the Moon. 4/*

And smile XRP-eyed faces also appear related to Egypt. In particular, to the Eye of Horus. https://t.co/i4rRzuQ0gZ 5/*