I couldn’t tweet a better description than the headline for this piece: After SolarWinds breach, lawmakers ask NSA for help in cracking Juniper cold case.
More from Law
2/ A pretty kickass reporter, Nicole Carr, recorded the video before the guy took it down. When she confronted him he insisted it was all a joke and of course he didn’t register in Georgia. But she checked and he had.
3/ This is Nicole Carr ...
\u201cIf that means changing your address for the next two months,so be it.I\u2019m doing that. I\u2019m moving to Georgia.\u201dOur 6 investigation reveals deleted video-a FL attorney telling GOP members how to move to GA,vote in runoffs. It\u2019s illegal.There\u2019s more,& an investigation @wsbtv #gapol pic.twitter.com/or2PgWQrT1
— Nicole Carr (@NicoleCarrWSB) December 2, 2020
4/ amazing. Here’s where she catches him 🤣🤣🤣🤣🤣🤣🤣🤣🤣🤔🤔
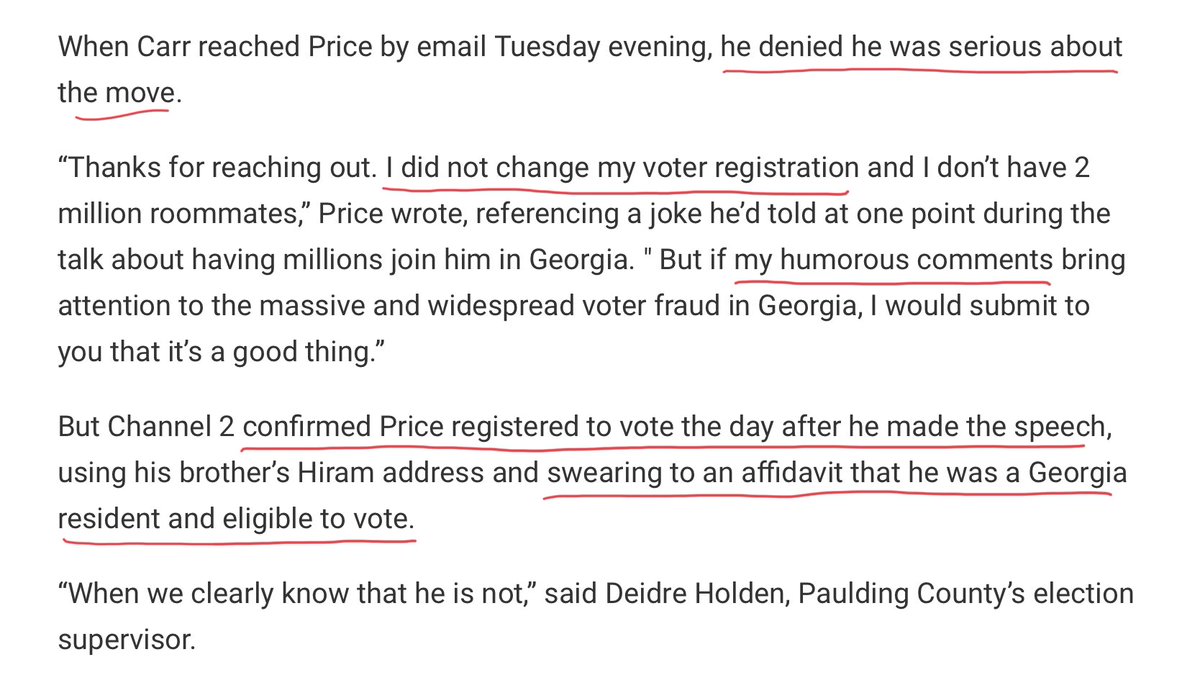
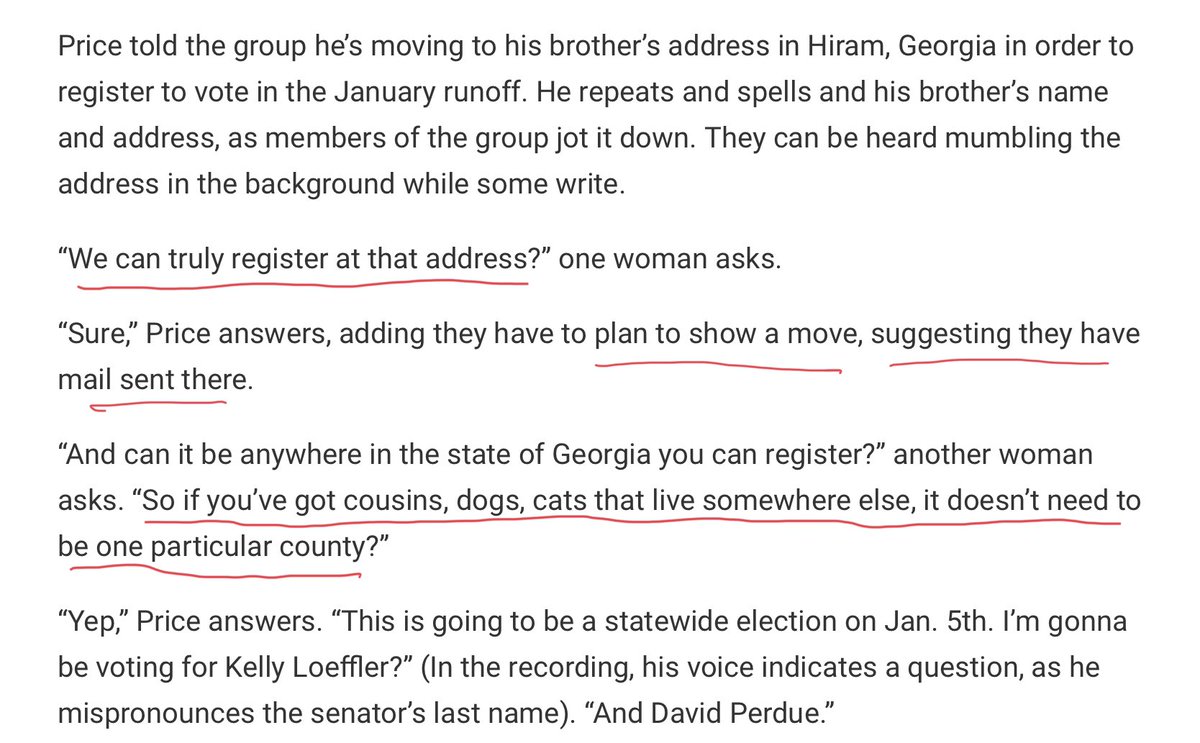
5/ Also on the video you’ve got these ladies saying, hey wait, this can’t really be legal can it? And he’s like, yeah totally cool. Then he advises on how to create a backstory for the fake move.
The Michigan case in the US Supreme Court originally filed by Sidney Powell and Lin Wood was just distributed today for Conference on 02/19/2021!
— Truth (@1foreverseeking) February 4, 2021
Feb 03 2021 DISTRIBUTED for Conference of 2/19/2021. https://t.co/jZO624pf7j
Wisconsin
The Wisconsin case in the US Supreme Court is also
— Truth (@1foreverseeking) February 4, 2021
distributed for Conference on 02/19/2021!https://t.co/zkpTubcG1C
Georgia
This Georgia case, originally filed by Lin Wood, is alo distributed for conference on February 21, 2021!https://t.co/l7j43v5pfD
— Truth (@1foreverseeking) February 4, 2021
Arizona
This Arizona case is also distributed for conference on Febraury 21, 2021!https://t.co/56g1Fphg2l
— Truth (@1foreverseeking) February 4, 2021
Another Pennsylvania case. This is the most important one in my opinion. It shows the Republican Legislature broke the law when they created a mail-in ballot law in October, 2019, which they knew was against the state
Another Pennsylvania case distributed for conference February 21, 2021.
— Truth (@1foreverseeking) February 4, 2021
Filed by a Republican Congressman who lost his seat because PA Republican Legislature illegally created a mail in ballot law October, 2019, against the Constitution of PA.https://t.co/RYJE6ENZGk
You May Also Like
He's STILL in charge of the Mueller investigation.
He's STILL refusing to hand over the McCabe memos.
He's STILL holding up the declassification of the #SpyGate documents & their release to the public.
I love a good cover story.......
The guy had a face-to-face with El Grande Trumpo himself on Air Force One just 2 days ago. Inside just about the most secure SCIF in the world.
And Trump came out of AF1 and gave ol' Rod a big thumbs up!
And so we're right back to 'that dirty rat Rosenstein!' 2 days later.
At this point it's clear some members of Congress are either in on this and helping the cover story or they haven't got a clue and are out in the cold.
Note the conflicting stories about 'Rosenstein cancelled meeting with Congress on Oct 11!"
First, rumors surfaced of a scheduled meeting on Oct. 11 between Rosenstein & members of Congress, and Rosenstein just cancelled it.
Rep. Andy Biggs and Rep. Matt Gaetz say DAG Rod Rosenstein cancelled an Oct. 11 appearance before the judiciary and oversight committees. They are now calling for a subpoena. pic.twitter.com/TknVHKjXtd
— Ivan Pentchoukov \U0001f1fa\U0001f1f8 (@IvanPentchoukov) October 10, 2018

























