FLASH: "Emergency Directive 21-01 calls on all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately."-@CISAgov Read more:

The attacker’s use multiple techniques to evade detection/obscure activity. The campaign is widespread affecting public & private organizations around the world.
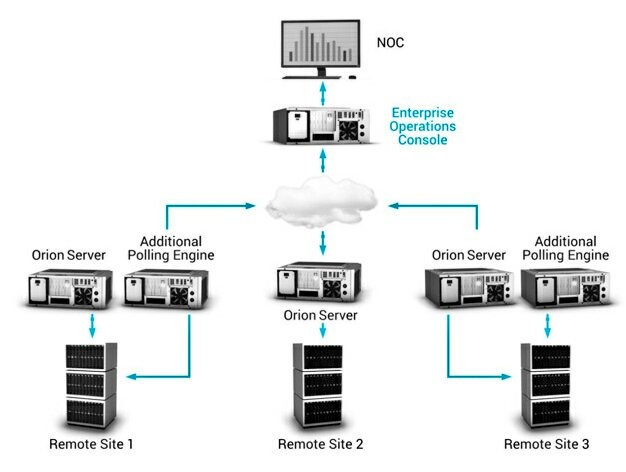
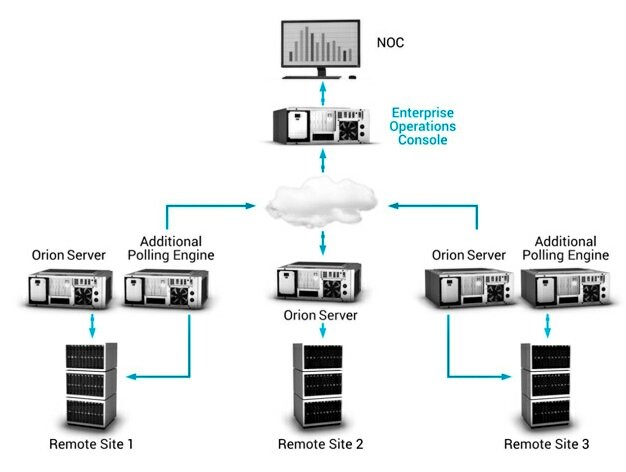
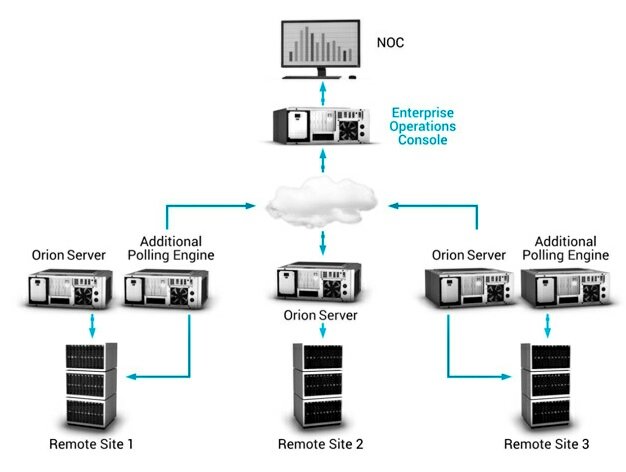
-Restrict scope of connectivity to endpoints from SolarWinds servers!
-Restrict the scope of accounts that have local administrator privileged on SolarWinds servers!
.... more
-Block Internet egress from servers or other endpoints with SolarWinds software.
-At MINIMUM changing passwords for accounts that have access to SolarWinds servers / infrastructure.
....more
-Review network device configurations for unexpected / unauthorized modifications. This is a proactive measure due to the scope of SolarWinds functionality.
-425+ of US Fortune 500 co's
-All of top 10 US telecom co's
-All 5 branches US Military
-Pentagon
-State Department
-NASA
-NSA
-USPS
-NOAA
-DOJ
-Office of POTUS
-Top 5 US accounting firms
-100's universities/colleges
List: https://t.co/N202UZdyjC
More from Internet
There are lots of problems with ad-tech:
* being spied on all the time means that the people of the 21st century are less able to be their authentic selves;
* any data that is collected and retained will eventually breach, creating untold harms;
1/

* data-collection enables for discriminatory business practices ("digital redlining");
* the huge, tangled hairball of adtech companies siphons lots (maybe even most) of the money that should go creators and media orgs; and
2/
* anti-adblock demands browsers and devices that thwart their owners' wishes, a capability that can be exploited for even more nefarious purposes;
That's all terrible, but it's also IRONIC, since it appears that, in addition to everything else, ad-tech is a fraud, a bezzle.
3/
Bezzle was John Kenneth Galbraith's term for "the magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." That is, a rotten log that has yet to be turned over.
4/
Bezzles unwind slowly, then all at once. We've had some important peeks under ad-tech's rotten log, and they're increasing in both intensity and velocity. If you follow @Chronotope, you've had a front-row seat to the
* being spied on all the time means that the people of the 21st century are less able to be their authentic selves;
* any data that is collected and retained will eventually breach, creating untold harms;
1/

* data-collection enables for discriminatory business practices ("digital redlining");
* the huge, tangled hairball of adtech companies siphons lots (maybe even most) of the money that should go creators and media orgs; and
2/
* anti-adblock demands browsers and devices that thwart their owners' wishes, a capability that can be exploited for even more nefarious purposes;
That's all terrible, but it's also IRONIC, since it appears that, in addition to everything else, ad-tech is a fraud, a bezzle.
3/
Bezzle was John Kenneth Galbraith's term for "the magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." That is, a rotten log that has yet to be turned over.
4/
Bezzles unwind slowly, then all at once. We've had some important peeks under ad-tech's rotten log, and they're increasing in both intensity and velocity. If you follow @Chronotope, you've had a front-row seat to the
The numbers are all fking fake, the metrics are bullshit, the agencies responsible for enforcing good practices are knowing bullshiters enforcing and profiting off all the fake numbers and none of the models make sense at scale of actual human users. https://t.co/sfmdrxGBNJ pic.twitter.com/thvicDEL29
— Aram Zucker-Scharff (@Chronotope) December 26, 2018
***THREAD***
I’ve been on the phone with colleagues about the hack all morning. None of us can figure out why #CISA chose this particular response to the breach. Couple of things struck us as curious.
The agencies targeted are not responding how you might expect...
I’ve been on the phone with colleagues about the hack all morning. None of us can figure out why #CISA chose this particular response to the breach. Couple of things struck us as curious.
The agencies targeted are not responding how you might expect...
JUST RELEASED: Emergency Directive 21-01 calls on all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately. Read more: https://t.co/VFZ81W2Ow7
— Cybersecurity and Infrastructure Security Agency (@CISAgov) December 14, 2020
Or, you could let us know when you figure out why it was trending yesterday and the users are complaining which is why Vice wrote about it. Why I'm saying what I am.
There's an assumption here that this problem is fixed bc it was already hacked.
It's not.
We have ppl freezing and dying in TX right now because some ppl who thought they were really smart never spoke to anyone with actual experience with energy systems in extreme cold climates.
Texans are waiting for a solution to a preventable problem.
Farmers are saying that now, not during a crisis, they have to wait for a JD tech to arrive to help them.
The assumption that bc SOME farmers said screw this and used hacked firmware to get around that obstacle doesn't mean that all farmers are doing that.
If all farmers were using hacked firmware we wouldn't be discussing this right now would we?
Of course no one has pointed out that another issue here is that no one at John Deere has figured out they don't have enough staff to quickly and reliably SOLVE problems.
The locked firmware is just one of many issues here.
By not giving people a fast solution they're causing this and other issues.
So what I'm saying is somebody at John Deere needs to examine all of this.
There's an assumption here that this problem is fixed bc it was already hacked.
It's not.
Let us know when you've found the supply chain hack that's already there
— SleeplessOrphan (@sleeplessorphan) February 20, 2021
We have ppl freezing and dying in TX right now because some ppl who thought they were really smart never spoke to anyone with actual experience with energy systems in extreme cold climates.
Texans are waiting for a solution to a preventable problem.
Farmers are saying that now, not during a crisis, they have to wait for a JD tech to arrive to help them.
The assumption that bc SOME farmers said screw this and used hacked firmware to get around that obstacle doesn't mean that all farmers are doing that.
If all farmers were using hacked firmware we wouldn't be discussing this right now would we?
Of course no one has pointed out that another issue here is that no one at John Deere has figured out they don't have enough staff to quickly and reliably SOLVE problems.
The locked firmware is just one of many issues here.
By not giving people a fast solution they're causing this and other issues.
So what I'm saying is somebody at John Deere needs to examine all of this.