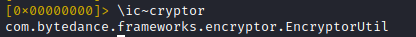
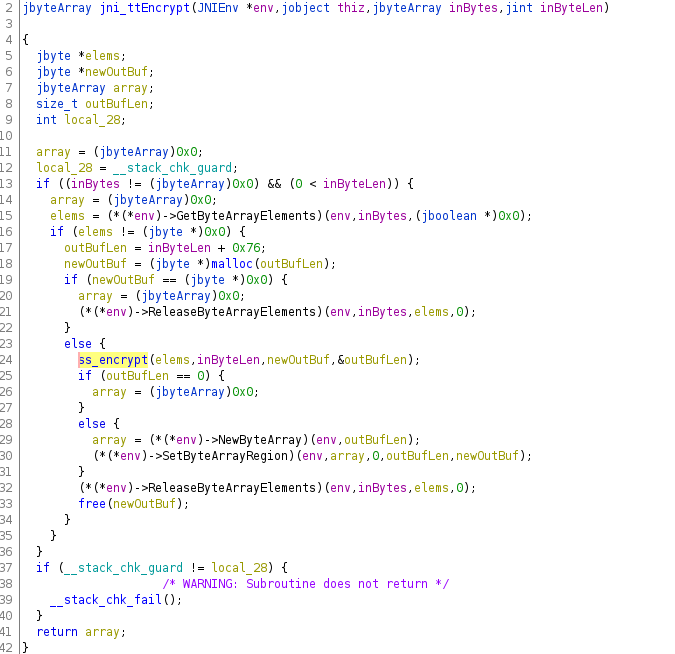
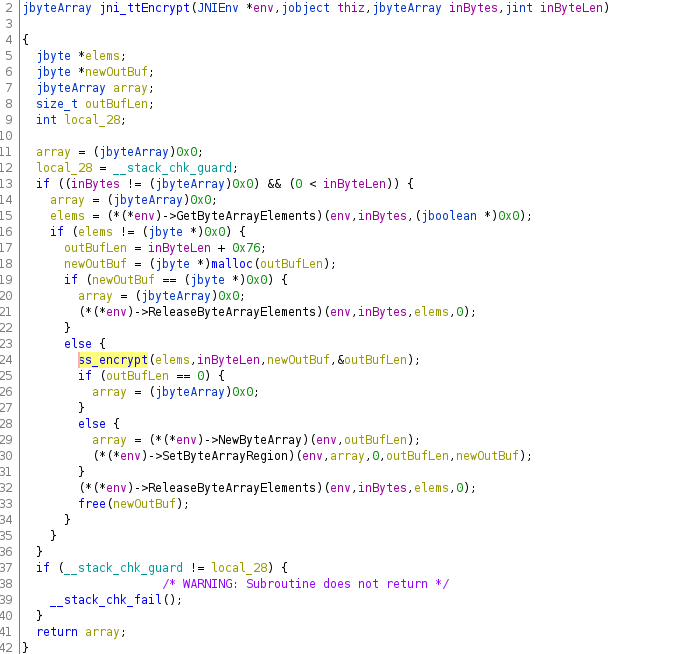
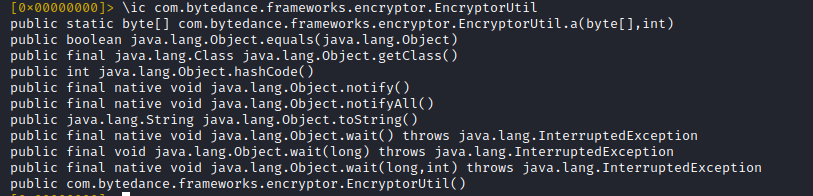
TikTok's (log data) encryption is accomplished by a native library. The Android Java code just serves as proxy function to the native function
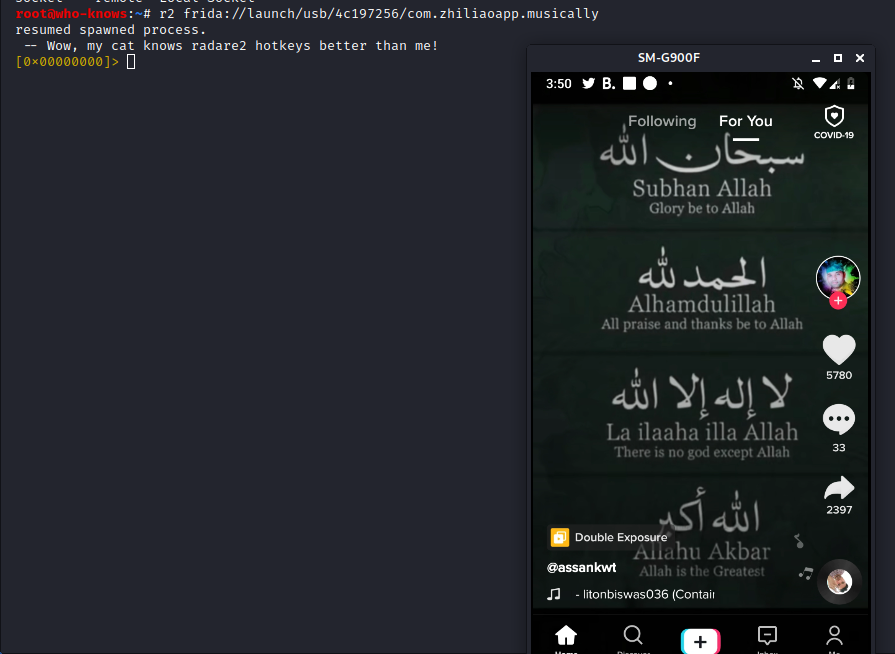
Okay, doing my first baby steps with r2frida (which combines the power of @radareorg and @fridadotre).
Gonna share my progress in this thread (live, so keep calm).
The goal: Runtime inspection of data sent out by TikTok !!before!! it gets encrypted
1/many
TikTok's (log data) encryption is accomplished by a native library. The Android Java code just serves as proxy function to the native function
https://t.co/T63vo3N4fw
1) Unlike raw C-functions, JNI functions like the one showcased above, receive pointers to complex Java objects .
F.e. a function receiving a String on the Java layer...
In order to retrieve a C-String, to go on working with it in the native code, some translation functionality is required. This functionality is provided by the ...
If you look at the example screenshot again, you see exactly this. Functions provided by the 'env' pointer are used to parse the Java function arguments (f.e. jByteArrays) ...
2) There are two ways to expose JNI methods from a native library:
a) export them with proper naming convention, so that JNI could recognize same on library load
b) use the JNI functionality 'registerNatives'...
The second method of registering methods is wel suited for obfuscated code, as the methods neither have to follow naming convention, nor do they have to be exported.
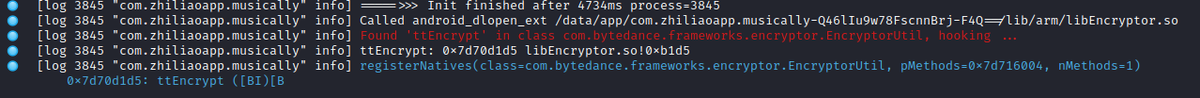
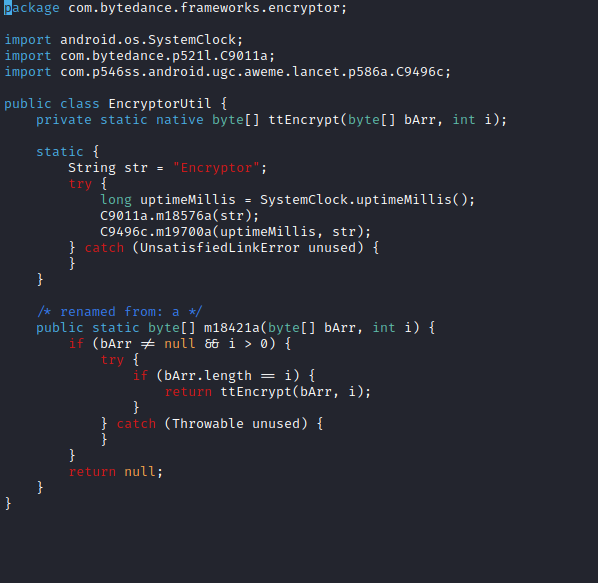
Internally, this data is forwarded to the native JNI method 'ttEncrypt'.
We already saw this signature in a previous screenshot
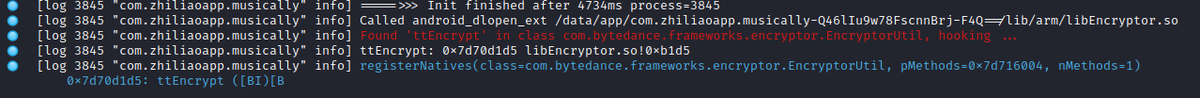
1) the call address of the native function implementation (0x7d70d1d5 in example)
2) The function name (ttEncrypt)
...
'(' start of parameters
'[B' byte[]
'I' int
')' end of parameters
'[B' byte[] (return value)
- the app is inspected on a physical device, running Android 9
- the device uses a !!32bit!! ARM application core
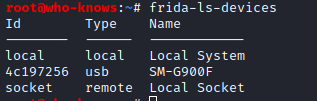
Now to get started, I already have the latest @fridadotre server running on my USB connected android device and 'frida-ls-device' shows it being ready-for-action
Instead of 'launch', two other options could be used:
- 'spawn' (like 'launch', but the process would not be resumed automatically after attaching)
Important: commands targeting the r2frida plugin have to be prefixed with '\'
The signature of the static method 'EncryptorUtil.a' should look familiar to us (if you read the first tweets). It represents the Java layer of the encryption method and is called 'a' in this version
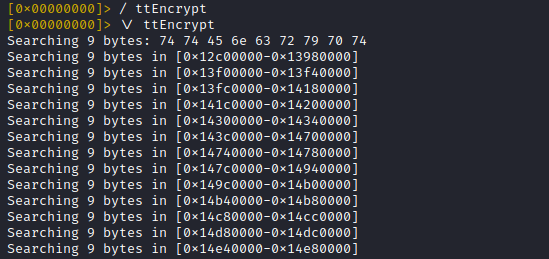
So lets search the whole address space for our native method name 'ttEncrypt'
Note: If you'd use r2's ascii search nothing would happen, you have to use the '\' prefix to search with r2frida
Reason: The memory region was not populated when r2 was started (encryption library was loaded after process launch)
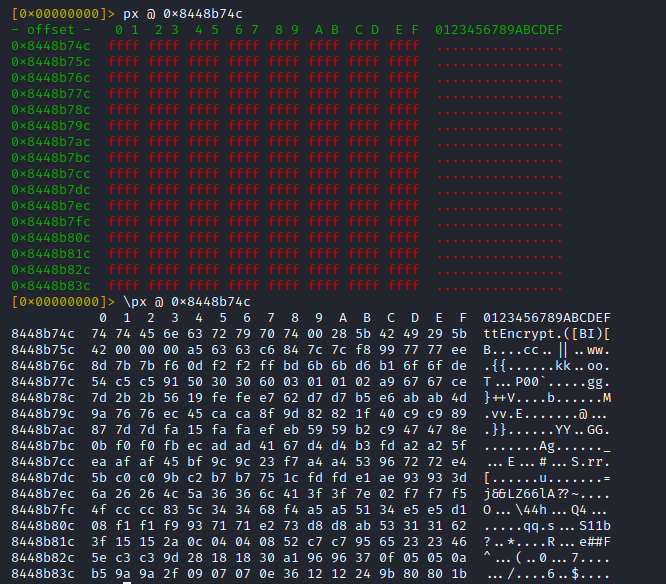
1) Quit r2
2) Open r2 with r2frida, again, but this time **attach** to the already running process
et voila ... the memory offset is mapped and dumpable with 'px' (without backslash prefix)
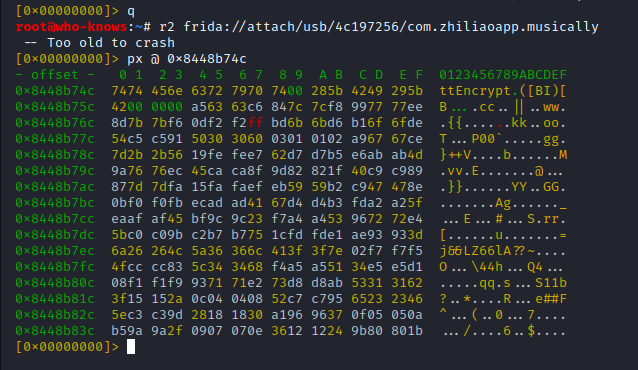
So chances are high, that this data is part of the structure which gets handed in to 'registerNatives'
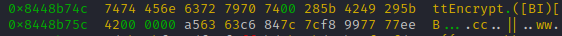
- method name (C-string)
- method signature (C-string)
- method pointer (native pointer)
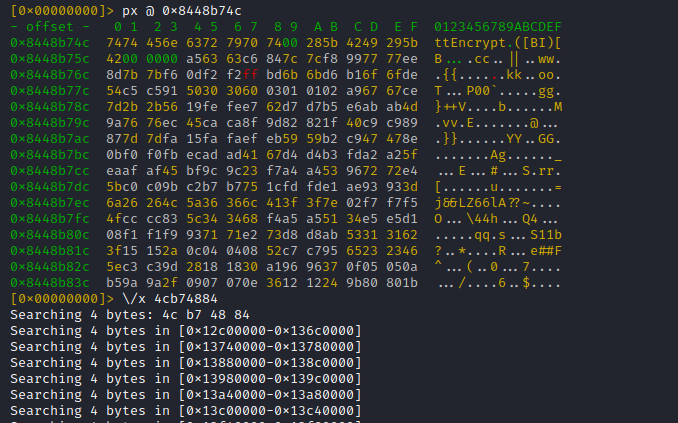
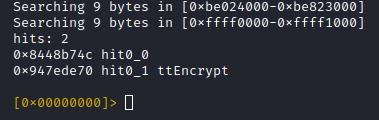
The result is promising: Only one hit, for a search across the whole address space:
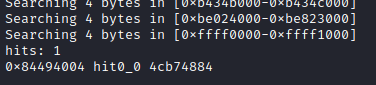
- 0x8448b74c (expected, method name pointer)
- 0x8448b756 (ptr to signature string, yay)
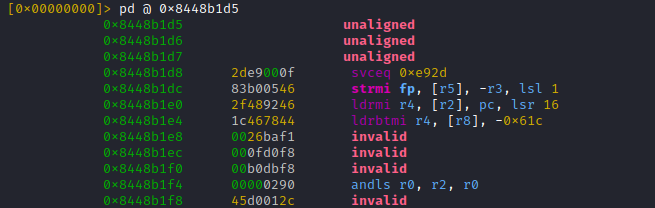
- 0x8448b1d5 (likely pointer to JNI method implementation)
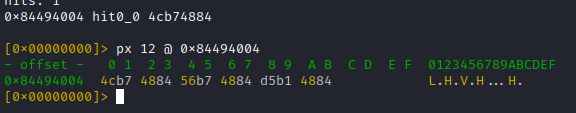
Arm 32 supports two instruction sets "ARM mode" (32bit) and "Thumb mode" (16bit) which could be used interchangebly
For ARM the LSB is 0 (even address)
For THUMB the LSB is 1 (odd address)
This means the function address 0x8448b1d5 homes code in THUMB mode (16bit), while the first instruction resides at 0x8448b1d4
(sorry if it gets a bit complicated, will be clear in a second)
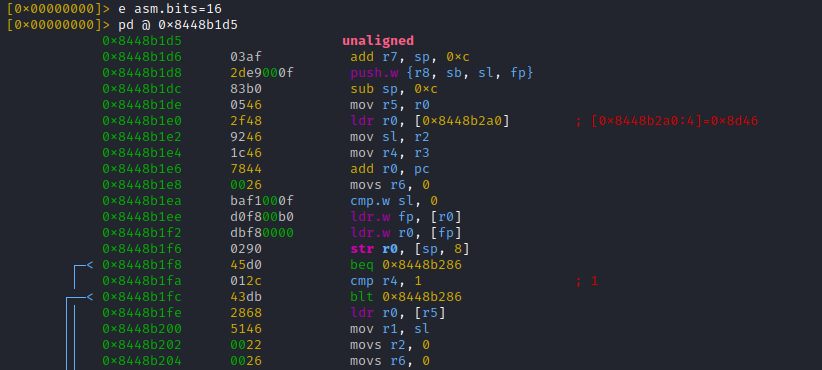
No seriously, as explained, on arm32 we have to disassemble at [THUMB mode address - 1] = 0x8448b1d4
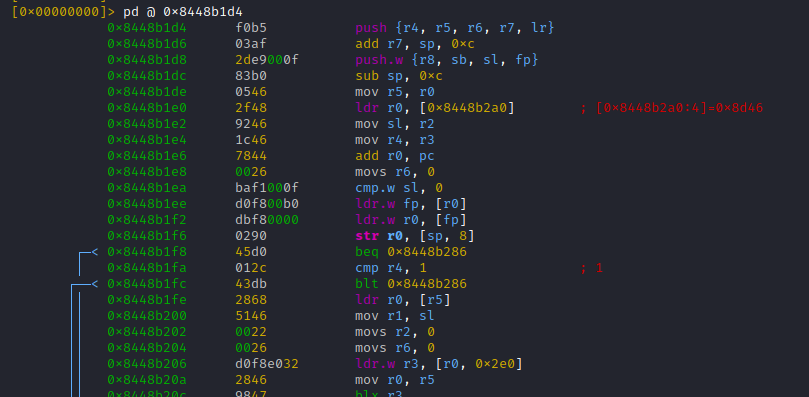
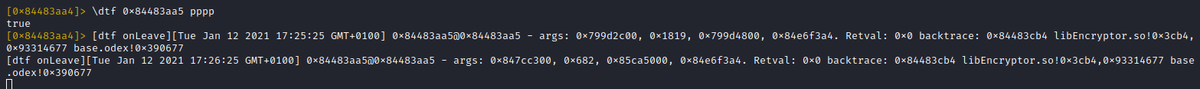
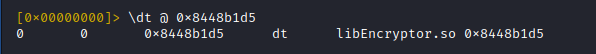
Now to get a feeling on how often this function is called, lets use 'r2frida' power to trace it.
Important: The thumb address has to be used here!!!
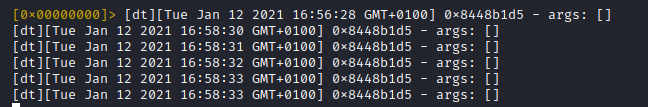
Some actions in the TikTok app ... trace logs for ttEncrypt-calls arrive
Trying to runtime-parse the function parameters, which represent Java object instances would be insane (maybe impossible)
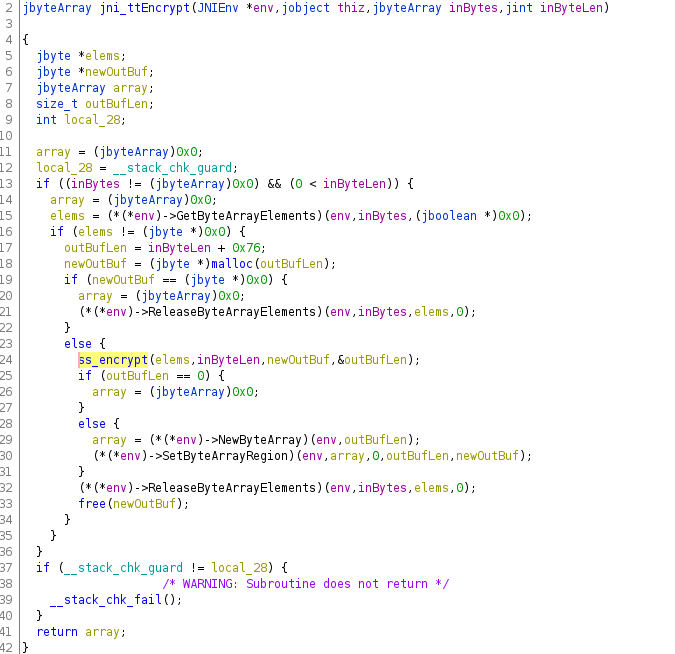
It would be way easier to runtime-inspect these
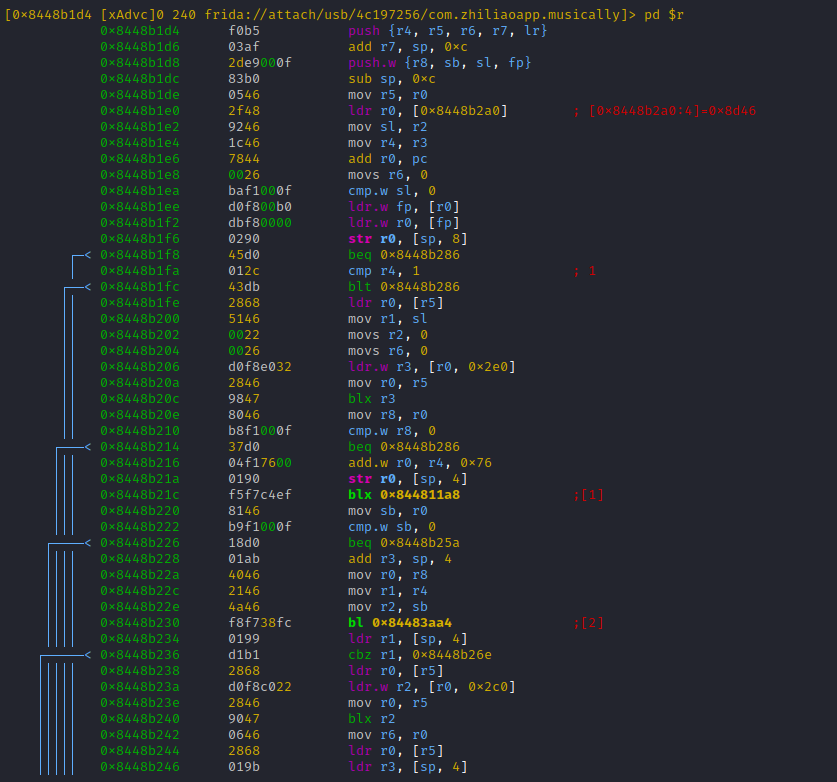
Hitting [alt+1] moves us straight to the marked branch offset:
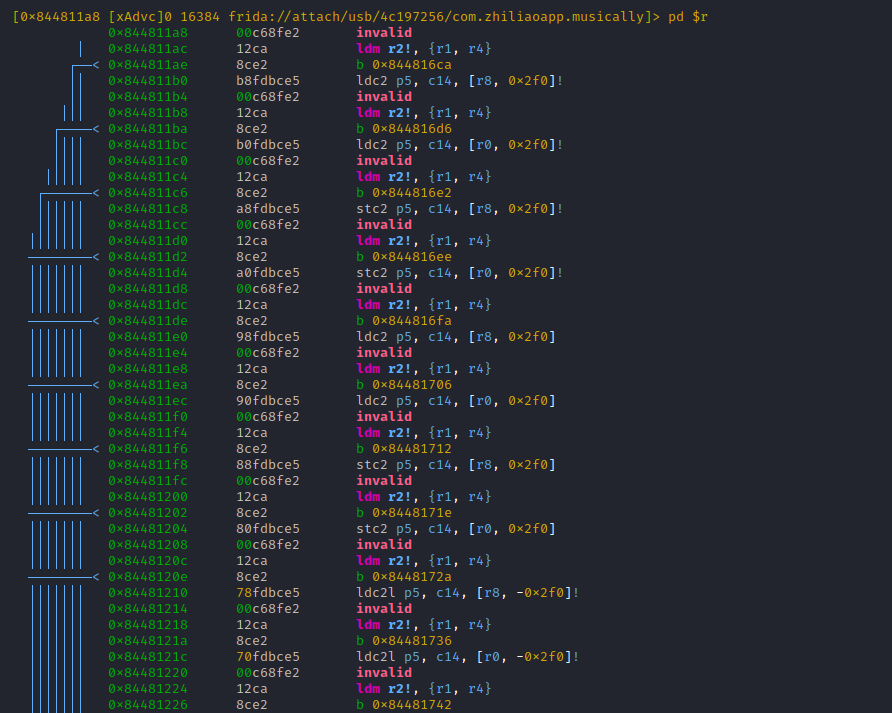
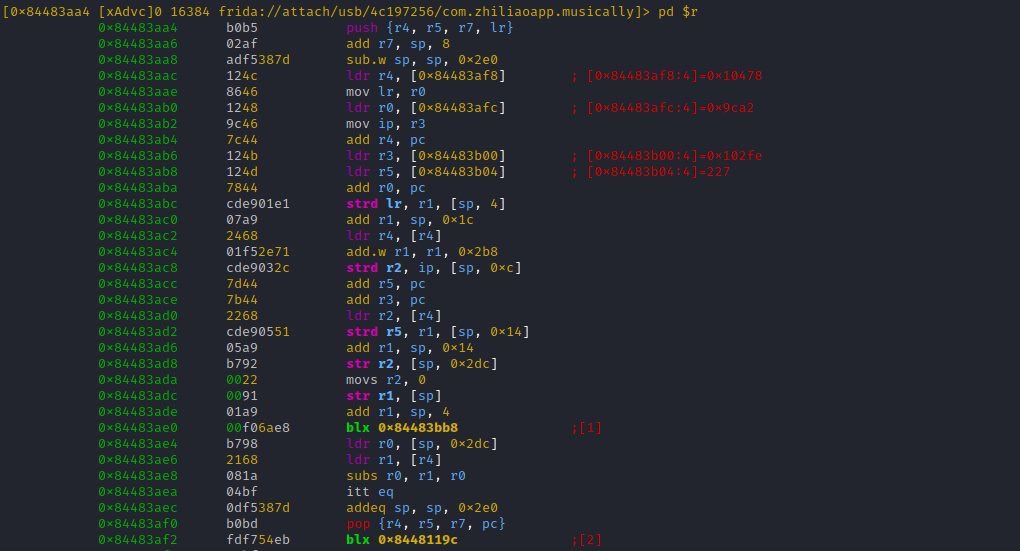
Hitting 'u' returns us to the parent function, followed by [alt+2] which brings us into the 2nd branch
More from Machine learning
You May Also Like
THE MEANING, SIGNIFICANCE AND HISTORY OF SWASTIK
The Swastik is a geometrical figure and an ancient religious icon. Swastik has been Sanatan Dharma’s symbol of auspiciousness – mangalya since time immemorial.

The name swastika comes from Sanskrit (Devanagari: स्वस्तिक, pronounced: swastik) &denotes “conducive to wellbeing or auspicious”.
The word Swastik has a definite etymological origin in Sanskrit. It is derived from the roots su – meaning “well or auspicious” & as meaning “being”.

"सु अस्ति येन तत स्वस्तिकं"
Swastik is de symbol through which everything auspicios occurs
Scholars believe word’s origin in Vedas,known as Swasti mantra;
"🕉स्वस्ति ना इन्द्रो वृधश्रवाहा
स्वस्ति ना पूषा विश्ववेदाहा
स्वस्तिनास्तरक्ष्यो अरिश्तनेमिही
स्वस्तिनो बृहस्पतिर्दधातु"

It translates to," O famed Indra, redeem us. O Pusha, the beholder of all knowledge, redeem us. Redeem us O Garudji, of limitless speed and O Bruhaspati, redeem us".
SWASTIK’s COSMIC ORIGIN
The Swastika represents the living creation in the whole Cosmos.

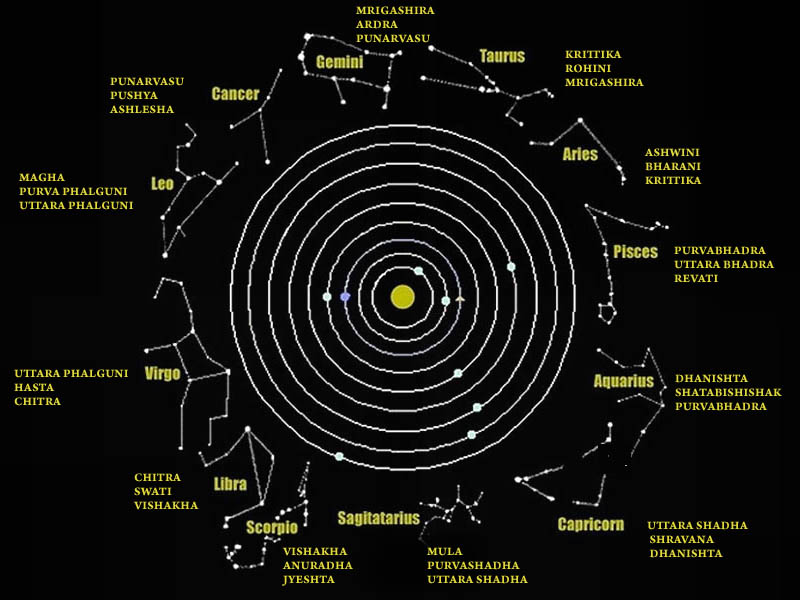
Hindu astronomers divide the ecliptic circle of cosmos in 27 divisions called https://t.co/sLeuV1R2eQ this manner a cross forms in 4 directions in the celestial sky. At centre of this cross is Dhruva(Polestar). In a line from Dhruva, the stars known as Saptarishi can be observed.
The Swastik is a geometrical figure and an ancient religious icon. Swastik has been Sanatan Dharma’s symbol of auspiciousness – mangalya since time immemorial.

The name swastika comes from Sanskrit (Devanagari: स्वस्तिक, pronounced: swastik) &denotes “conducive to wellbeing or auspicious”.
The word Swastik has a definite etymological origin in Sanskrit. It is derived from the roots su – meaning “well or auspicious” & as meaning “being”.

"सु अस्ति येन तत स्वस्तिकं"
Swastik is de symbol through which everything auspicios occurs
Scholars believe word’s origin in Vedas,known as Swasti mantra;
"🕉स्वस्ति ना इन्द्रो वृधश्रवाहा
स्वस्ति ना पूषा विश्ववेदाहा
स्वस्तिनास्तरक्ष्यो अरिश्तनेमिही
स्वस्तिनो बृहस्पतिर्दधातु"

It translates to," O famed Indra, redeem us. O Pusha, the beholder of all knowledge, redeem us. Redeem us O Garudji, of limitless speed and O Bruhaspati, redeem us".
SWASTIK’s COSMIC ORIGIN
The Swastika represents the living creation in the whole Cosmos.

Hindu astronomers divide the ecliptic circle of cosmos in 27 divisions called https://t.co/sLeuV1R2eQ this manner a cross forms in 4 directions in the celestial sky. At centre of this cross is Dhruva(Polestar). In a line from Dhruva, the stars known as Saptarishi can be observed.