That comparison deserves to be drawn and it raises some very important questions.
I have seen so many people (including folks on #lawtwitter) comparing what happened at the Capitol yesterday with the violence and property damage that happened in some cities during protests last summer.
Let me explain what is wrong with that analogy . . . . .
That comparison deserves to be drawn and it raises some very important questions.
Very different reaction then. But kudos to those who\u2019ve consistently condemned riots. I hope, if nothing else, today\u2019s violence means we are all on the same page now. https://t.co/JhWadB80So
— Andy Grewal (@AndyGrewal) January 7, 2021
This is a pretty basic social and legal concept.
The people at BLM protests were trying to get changes made to policing practices.
The people at the Capitol were trying to stop Congress from certifying an election.
There is also a huge difference in how those actions came about--specifically the role that public officials played in the turmoil and protests that led to the storming of the Capitol.
They have been leading the charge to challenge the result.
They have been engaging in rhetoric that talks about violence and unrest.
They fanned these flames.
He told them to march to the Capitol, and he repeated it multiple times.
Did they give the protestors a fist pump like Josh Hawley did, as he was heading in to try and overturn the election using frivolous legal arguments?
More from Legal
All six are associated with the far-right #OathKeepers militia.
THREAD 1/
Story: https://t.co/abZlcVyaR6

2/ On January 5th, Stone appeared at the Supreme Court, glad-handing and being driven in a go-kart. Later he attended a rally near the White House.
As the @nytimes team shows, his security entourage featured a host of #OathKeepers...
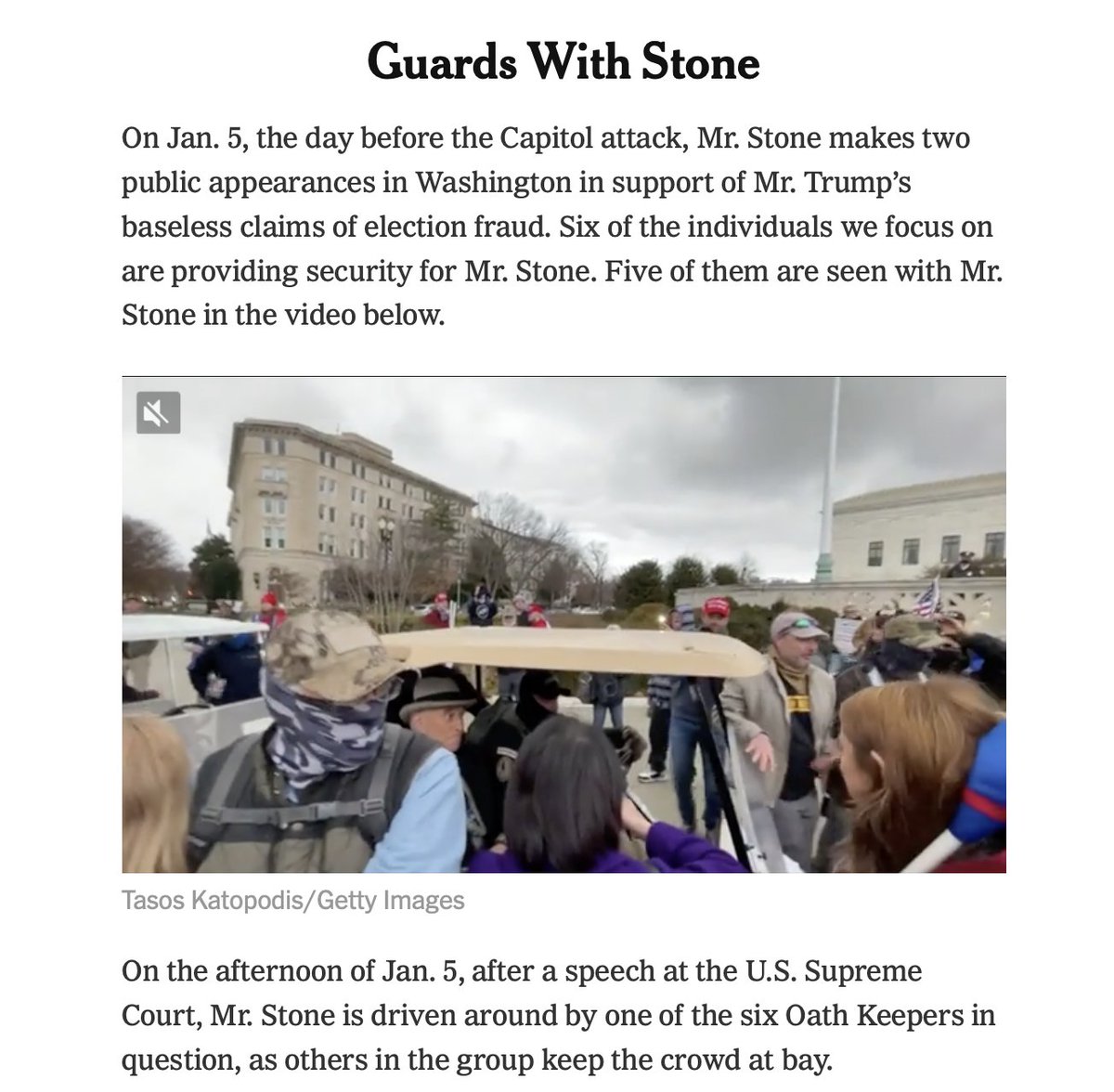
3/ In the morning of the 6th, Stone stood outside the Willard InterContinental hotel, again flanked by men associated with the #OathKeepers.
Some of them, like Rob Minuta, have been named in prior

NEW: Rob Minuta guarded Roger Stone Jan 6th...& was later seen at #Capitol siege..
— John Scott-Railton (@jsrailton) February 7, 2021
Now we know he has a history of escorting Trump allies like Flynn & Alex Jones. Also seen in December w/indicted Proud Boy #Spazzo.
THREAD
By @arawnsley
Link: https://t.co/8t38iOmgYP pic.twitter.com/dnRYZGuBCO
4/ Interesting detail: while scrutinizing the video of Roger Stone I spotted Rudy Giuliani exiting the same hotel.
Giuliani is accompanied by a man wearing the same outfit as Trump supporter John Eastman & other not-yet ID'd people.
Video source: https://t.co/Rure8TiQTp

5/ Now to the #Capitol: We see a several of Roger Stone's #OathKeeper guards amidst a larger group yelling at police. Video surfaced by the @CTExposers team.👇👇
https://t.co/NWsONDz0OA

Here's the footage of Roberto Minuta throwing a tantrum at the police, 1/6 at the east side of the Capitol (5:16 in the Youtube video link).
— Capitol Terrorists Exposers (@CTExposers) February 10, 2021
\u27a1\ufe0fhttps://t.co/rulMuaftCm pic.twitter.com/wz6A4zQLYT
Including highly decorated ex-members of the military.
The double wrist ties, tasers, discarded weapons all show an intention to go much further than they got
BREAKING I can now confirm Male #2 w/ restraints is highly decorated combat vet & @AF_Academy graduate Lt. Colonel. Ret. Larry Brock of Texas.
— John Scott-Railton (@jsrailton) January 9, 2021
Releasing his name now after 24h of collaboration w/@RonanFarrow & his investigations team to confirm.https://t.co/nog9HI7DzX pic.twitter.com/ClHImsFucM
Seems so ordinary, becoming Lieutenant Commander Brock in the US Airforce ...yet the conversion from the ordinary into the extremist will make a fascinating study for psychologists @RichardBentall

His claim that he picked up the wrist ties “someone” had dropped so he could hand them into police is laughable.
And when you think about it rather cowardly. Can’t even take responsibility for what he has done.
Who else were involved in the planning? Which mates of his?
The attention to detail in making the links is impressive.
There’s going to be a lot more doors knocked in in the next few weeks.
How high and how deep into the Trump establishment does it go.?

H/T @k8tshires for this summary from CNN
If the people involved in this insurrection succeeded where would the establishment face of the movement be?
I suspect not making the denouncements they are now that it
Prosecutors alleged Barnett was carrying a stun gun. He's charged with entering a restricted area w/ a weapon, violent entry/disorderly conduct, and theft. There isn't anything on the docket indicating what the govt/Barnett will be seeking as far as detention v. release

We're still waiting for the Richard Barnett detention hearing to start in Arkansas. Meanwhile, follow @o_ema for updates on initial appearances in DC federal court today for a few of the Capitol insurrection arrestees -->
Listening in on more hearings: The 1st is Kevin Loftus, WI, arrested for participating in the riots at the Capitol, charged w Class A misdemeanor. Judge decreed he is released on the condition that he does not return to DC, doesn't drink or do drugs, and doesn't break any laws.
— Ema O'Connor (@o_ema) January 15, 2021
Richard Barnett's detention hearing is underway in Arkansas — Judge Erin Wiedemann will decide if Barnett should stay behind bars. The first witness is FBI special agent Jonathan Willett, who was involved in the Capitol riot investigation
FBI agent walks the judge through surveillance videos that the agent says show Barnett walking in and out of Nancy Pelosi's office, with a "walking stick Taser" on his hip, as well as the widely disseminated photos of Barnett sitting in Pelosi's chair with his feet up
You May Also Like
The Swastik is a geometrical figure and an ancient religious icon. Swastik has been Sanatan Dharma’s symbol of auspiciousness – mangalya since time immemorial.

The name swastika comes from Sanskrit (Devanagari: स्वस्तिक, pronounced: swastik) &denotes “conducive to wellbeing or auspicious”.
The word Swastik has a definite etymological origin in Sanskrit. It is derived from the roots su – meaning “well or auspicious” & as meaning “being”.

"सु अस्ति येन तत स्वस्तिकं"
Swastik is de symbol through which everything auspicios occurs
Scholars believe word’s origin in Vedas,known as Swasti mantra;
"🕉स्वस्ति ना इन्द्रो वृधश्रवाहा
स्वस्ति ना पूषा विश्ववेदाहा
स्वस्तिनास्तरक्ष्यो अरिश्तनेमिही
स्वस्तिनो बृहस्पतिर्दधातु"

It translates to," O famed Indra, redeem us. O Pusha, the beholder of all knowledge, redeem us. Redeem us O Garudji, of limitless speed and O Bruhaspati, redeem us".
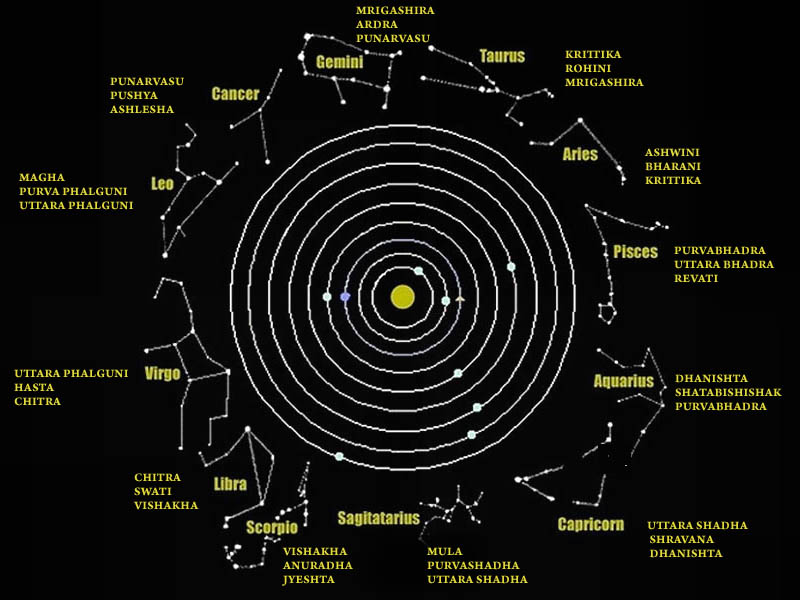
SWASTIK’s COSMIC ORIGIN
The Swastika represents the living creation in the whole Cosmos.

Hindu astronomers divide the ecliptic circle of cosmos in 27 divisions called https://t.co/sLeuV1R2eQ this manner a cross forms in 4 directions in the celestial sky. At centre of this cross is Dhruva(Polestar). In a line from Dhruva, the stars known as Saptarishi can be observed.