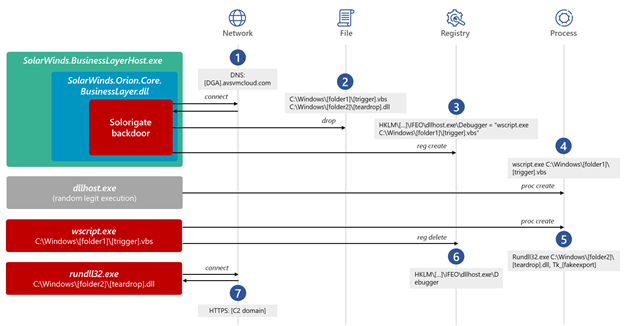
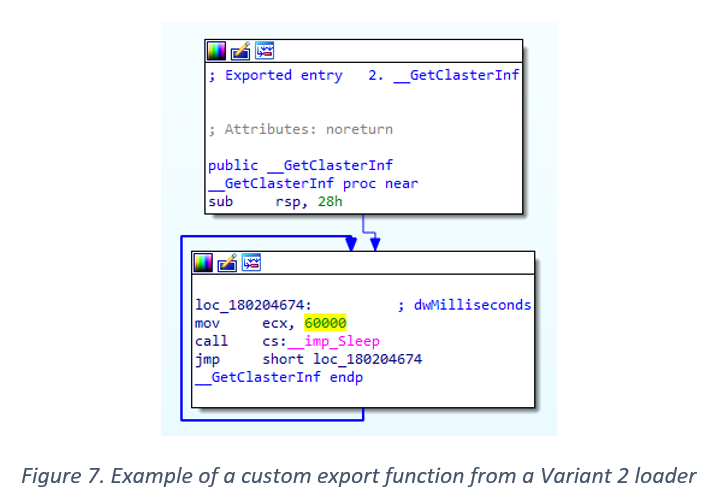
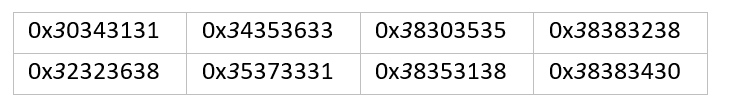
The missing link between the Solorigate backdoor and the custom #CobaltStrike loaders observed during the #Solorigate is an Image File Execution Options (IFEO) Debugger registry value created for the legitimate process dllhost.exe (ATT&CK ID: T1546.012).
As part of our commitment to keeping our customers/community protected & informed, we are releasing a blog that shines light on transition between Stage 1 and 2 of #Solorigate/#SUNBURST campaign, custom Cobalt Strike loaders, post-exploit. artifacts, IOCs: https://t.co/b0ReHMa63u
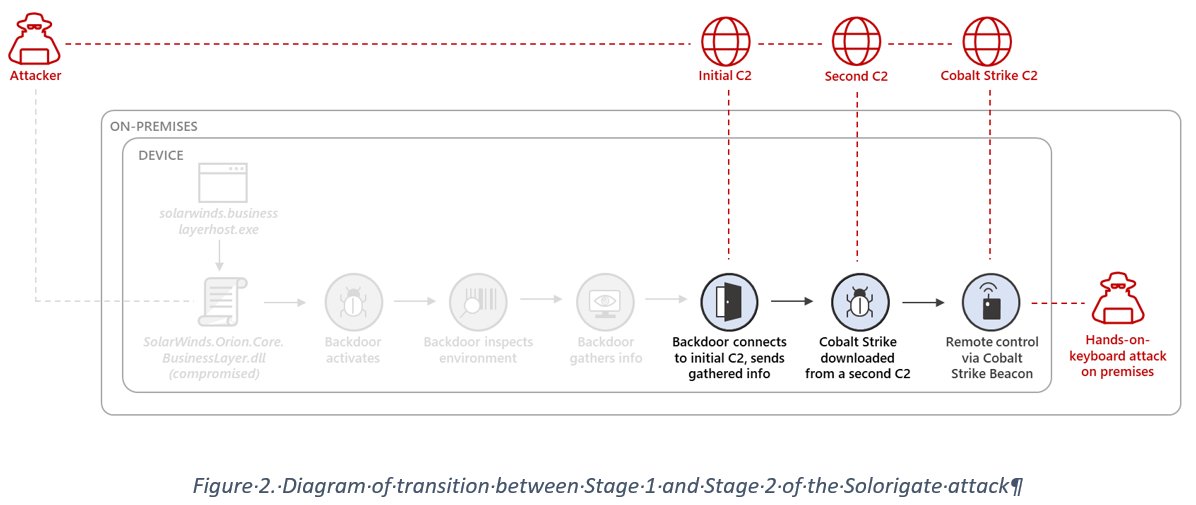
The missing link between the Solorigate backdoor and the custom #CobaltStrike loaders observed during the #Solorigate is an Image File Execution Options (IFEO) Debugger registry value created for the legitimate process dllhost.exe (ATT&CK ID: T1546.012).
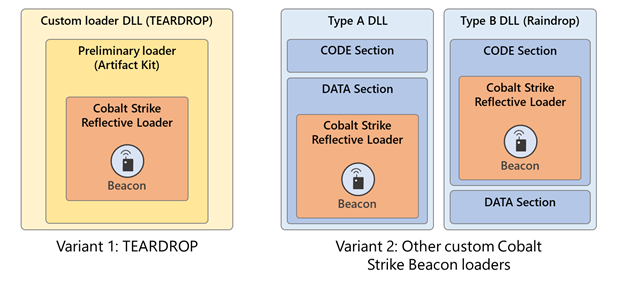
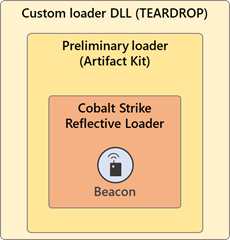
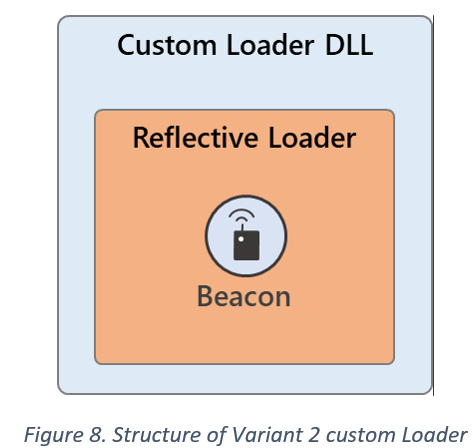
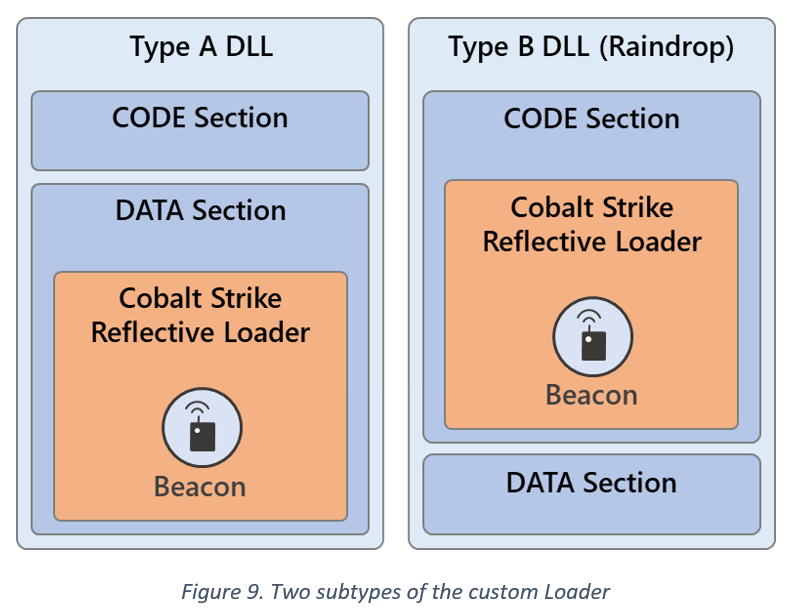
Type A: Decodes/Loads CS's RL from the DLL’s DATA section (detected as Trojan:Win64/Solorigate.SC!dha)
Type B: De-obfuscates/Loads RL from the DLL’s CODE section (aka #Raindrop, detected as Trojan:Win64/Solorigate.SB!dha).
The custom loader DLLs were introduced to compromised systems between the hours of 8:00 AM and 5:00 PM UTC. In one intrusion, the first 2nd stage custom loader (TEARDROP) was introduced to the environment by SolarWinds.BusinessLayerHost.exe at ~ 10:00 AM UTC.
More from Business
1/An interesting thing happened tonight. I was scrolling through clubhouse and found WileyCEO, Godfather of Grime (kicked off Twitter in July for antisemitic tweets) speaking. So I tweeted this (and included a screen shot, later deleted as I found out TOS don't allow it ...
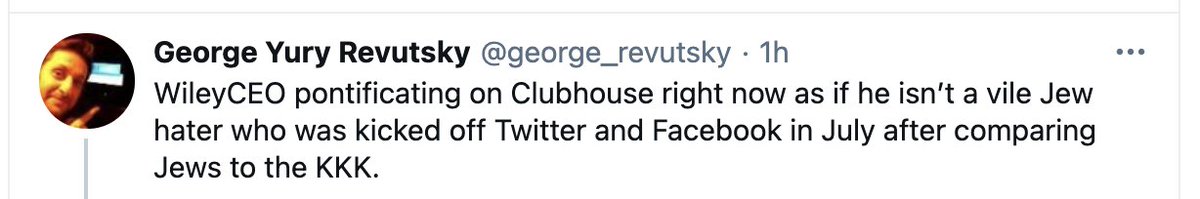
2/ ... and several folks also asked me to remove it which I promptly did afterwards).... Coming into the CH room, I fully intended to confront him about how hurtful his comments in July were. But as I listened to the folks in the room, I decided to go a different direction ....
3/ the conversation jumped around, covered many topics and there were between 8-14 people up on stage. But a recurring thread was discussion of racism, bigotry, comparison of it in the US vs UK vs elsewhere.
4/ when I got a chance to speak, I had 5 bullets written down: a) we should harness technology and capitalism to make reparations for what America did to Black people. I gave https://t.co/SlrW8zCd58 (a project a couple friends co-started) as an example) ...
5/ b) capitalism and product know-how and technology can be harnessed for social justice c) historically oppressed minorities need to stick together and lastly, d) "Wiley, how could you say such hurtful things about Jews as a people?" That's what I had ready to say, anyway.

2/ ... and several folks also asked me to remove it which I promptly did afterwards).... Coming into the CH room, I fully intended to confront him about how hurtful his comments in July were. But as I listened to the folks in the room, I decided to go a different direction ....
3/ the conversation jumped around, covered many topics and there were between 8-14 people up on stage. But a recurring thread was discussion of racism, bigotry, comparison of it in the US vs UK vs elsewhere.
4/ when I got a chance to speak, I had 5 bullets written down: a) we should harness technology and capitalism to make reparations for what America did to Black people. I gave https://t.co/SlrW8zCd58 (a project a couple friends co-started) as an example) ...
5/ b) capitalism and product know-how and technology can be harnessed for social justice c) historically oppressed minorities need to stick together and lastly, d) "Wiley, how could you say such hurtful things about Jews as a people?" That's what I had ready to say, anyway.
So I'd recommend reading this thread from Dave, but I thought about some of these policies, and how they fit into the whole, a lot, and want to offer a different interpretation.
I think California is world leading on progressivism that doesn't ask anyone to give anything up, or accept any major change, right now.
That's what I mean by symbolically progressive, operationally conservative.
Take the 100% renewable energy standard. As @leahstokes has written, these policies often fail in practice. I note our leadership on renewable energy in the piece, but the kind of politics we see on housing and transportation are going foil that if they don't change.
Creating a statewide consumer financial protection agency is great! But again, you're not asking most voters to give anything up or accept any actual changes.
I don't see that as balancing the scales on, say, high-speed rail.
CA is willing to vote for higher taxes, new agencies, etc. It was impressive when LA passed Measure H, a new sales tax to fund homeless shelters. And depressing to watch those same communities pour into the streets to protest shelters being placed near them. That's the rub.
It's very in vogue to bash California and this doesn't even reach to some things that deserve scorn, like the continuing control of the Western States Petroleum Association and the state Chamber of Commerce in policymaking. And yet-https://t.co/vHZ6GM7QF8
— David Dayen (@ddayen) February 11, 2021
I think California is world leading on progressivism that doesn't ask anyone to give anything up, or accept any major change, right now.
That's what I mean by symbolically progressive, operationally conservative.
Take the 100% renewable energy standard. As @leahstokes has written, these policies often fail in practice. I note our leadership on renewable energy in the piece, but the kind of politics we see on housing and transportation are going foil that if they don't change.
Creating a statewide consumer financial protection agency is great! But again, you're not asking most voters to give anything up or accept any actual changes.
I don't see that as balancing the scales on, say, high-speed rail.
CA is willing to vote for higher taxes, new agencies, etc. It was impressive when LA passed Measure H, a new sales tax to fund homeless shelters. And depressing to watch those same communities pour into the streets to protest shelters being placed near them. That's the rub.
You May Also Like
1/“What would need to be true for you to….X”
Why is this the most powerful question you can ask when attempting to reach an agreement with another human being or organization?
A thread, co-written by @deanmbrody:
2/ First, “X” could be lots of things. Examples: What would need to be true for you to
- “Feel it's in our best interest for me to be CMO"
- “Feel that we’re in a good place as a company”
- “Feel that we’re on the same page”
- “Feel that we both got what we wanted from this deal
3/ Normally, we aren’t that direct. Example from startup/VC land:
Founders leave VC meetings thinking that every VC will invest, but they rarely do.
Worse over, the founders don’t know what they need to do in order to be fundable.
4/ So why should you ask the magic Q?
To get clarity.
You want to know where you stand, and what it takes to get what you want in a way that also gets them what they want.
It also holds them (mentally) accountable once the thing they need becomes true.
5/ Staying in the context of soliciting investors, the question is “what would need to be true for you to want to invest (or partner with us on this journey, etc)?”
Multiple responses to this question are likely to deliver a positive result.
Why is this the most powerful question you can ask when attempting to reach an agreement with another human being or organization?
A thread, co-written by @deanmbrody:
Next level tactic when closing a sale, candidate, or investment:
— Erik Torenberg (@eriktorenberg) February 27, 2018
Ask: \u201cWhat needs to be true for you to be all in?\u201d
You'll usually get an explicit answer that you might not get otherwise. It also holds them accountable once the thing they need becomes true.
2/ First, “X” could be lots of things. Examples: What would need to be true for you to
- “Feel it's in our best interest for me to be CMO"
- “Feel that we’re in a good place as a company”
- “Feel that we’re on the same page”
- “Feel that we both got what we wanted from this deal
3/ Normally, we aren’t that direct. Example from startup/VC land:
Founders leave VC meetings thinking that every VC will invest, but they rarely do.
Worse over, the founders don’t know what they need to do in order to be fundable.
4/ So why should you ask the magic Q?
To get clarity.
You want to know where you stand, and what it takes to get what you want in a way that also gets them what they want.
It also holds them (mentally) accountable once the thing they need becomes true.
5/ Staying in the context of soliciting investors, the question is “what would need to be true for you to want to invest (or partner with us on this journey, etc)?”
Multiple responses to this question are likely to deliver a positive result.




















